Tech
I Love This Dart Counter for Local and Online Matches
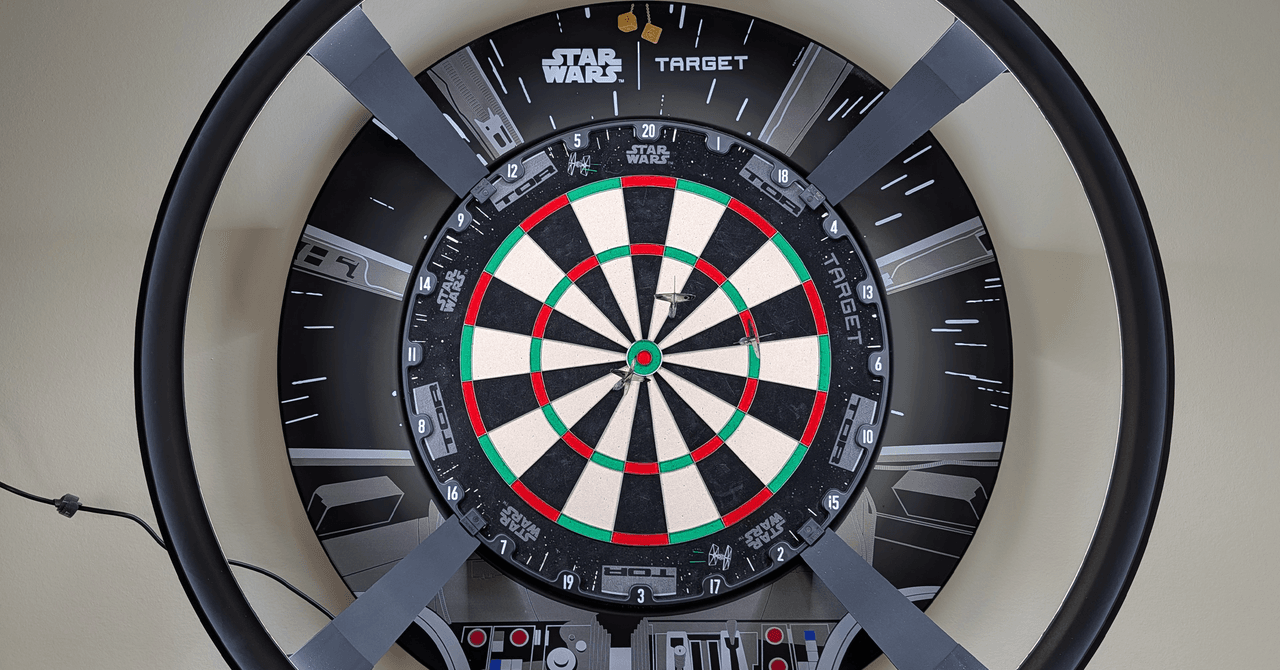
I never liked playing darts, but I did a complete 180 with this auto-scoring system. This gadget has ignited my newfound love of the old pub favorite. It’s a light ring with four hi-def cameras that slots onto your board. Connect with the DartCounter app via Wi-Fi and you get effortless automatic scoring with an announcer calling your points and telling you what you need to check out.
I’ve been testing the Target Darts Omni Auto Scoring System for the last few weeks, playing locally on my own and with family, and playing the odd match online. It’s a pricey system, but for darts fans and players looking to improve their game, it could be worth the investment. As a casual fan, I’ve found that a wee game of darts is a great way to unwind at the end of your day.
Stepping Up to the Oche
The Target Darts Omni Auto Scoring System pairs with the DartCounter app (Android or iOS). It’s quick and easy to put together, attaching to your board via magnetic legs, but you will need to run the power cable to an outlet. Connect to Wi-Fi, run a short calibration, and it’s time to play. I tested with Target’s Star Wars Millennium Falcon Surround and Dartboard ($200 or £150) and a set of Darth Vader Darts ($340 or £250)—both amazing Star Wars gifts for the fan in your life—but it should work with most boards and any darts.
The LED ring lights up the dartboard beautifully. The four HD cameras accurately record the score for each dart thrown. The DartCounter app compiles comprehensive statistics on your play. You can configure all the match parameters in the app for a tailor-made session, and there are also multiple practice modes and games, such as Around the Clock, where you have to hit each number in sequence and then the bull’s-eye, and Bob’s 27, where you start with 27 points and have to hit the doubles shown.
Online multiplayer is perhaps the biggest selling point, and you can find matches or create your own lobby in the DartCounter app. I never had any trouble finding a match, and there were well over 100 live matches in progress every time I checked. You get three free online matches every week. To unlock all the features, including tournaments, unlimited online games, more detailed stats, and the Master Caller using your name, you must subscribe for $6 a month or $40 a year (£6 and £40 in the UK). You get a three-month free trial with the system. Local play is free, with the exception of a couple of games (121 Checkout and Halve It), so you don’t need to subscribe.
I’ve played loads of games over the past few weeks, but I had the most fun playing a tournament with my brother. We had a dartboard in the garage when I was a teen and spent hours throwing darts, but neither of us had played in years. After much hilarity at how inept we had become and plenty of reminiscing, we both got our eye in, and things became competitive. I won the best-of-five classic 501 matches, but then my brother beat me at Around the Clock (I got stuck on the bull’s-eye).
Tech
Moltbook, the Social Network for AI Agents, Exposed Real Humans’ Data

An analysis by WIRED this week found that ICE and CBP’s face recognition app Mobile Fortify, which is being used to identify people across the United States, isn’t actually designed to verify who people are and was only approved for Department of Homeland Security use by relaxing some of the agency’s own privacy rules.
WIRED took a close look at highly militarized ICE and CBP units that use extreme tactics typically seen only in active combat. Two agents involved in the shooting deaths of US citizens in Minneapolis are reportedly members of these paramilitary units. And a new report from the Public Service Alliance this week found that data brokers can fuel violence against public servants, who are facing more and more threats but have few ways to protect their personal information under state privacy laws.
Meanwhile, with the Milano Cortina Olympic Games beginning this week, Italians and other spectators are on edge as an influx of security personnel—including ICE agents and members of the Qatari Security Forces—descend on the event.
And there’s more. Each week, we round up the security and privacy news we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
AI has been touted as a super-powered tool for finding security flaws in code for hackers to exploit or for defenders to fix. For now, one thing is confirmed: AI creates a lot of those hackable bugs itself—including a very bad one revealed this week in the AI-coded social network for AI agents known as Moltbook.
Researchers at the security firm Wiz this week revealed that they’d found a serious security flaw in Moltbook, a social network intended to be a Reddit-like platform for AI agents to interact with one another. The mishandling of a private key in the site’s JavaScript code exposed the email addresses of thousands of users along with millions of API credentials, allowing anyone access “that would allow complete account impersonation of any user on the platform,” as Wiz wrote, along with access to the private communications between AI agents.
That security flaw may come as little surprise given that Moltbook was proudly “vibe-coded” by its founder, Matt Schlicht, who has stated that he “didn’t write one line of code” himself in creating the site. “I just had a vision for the technical architecture, and AI made it a reality,” he wrote on X.
Though Moltbook has now fixed the site’s flaw discovered by Wiz, its critical vulnerability should serve as a cautionary tale about the security of AI-made platforms. The problem often isn’t any security flaw inherent in companies’ implementation of AI. Instead, it’s that these firms are far more likely to let AI write their code—and a lot of AI-generated bugs.
The FBI’s raid on Washington Post reporter Hannah Natanson’s home and search of her computers and phone amid its investigation into a federal contractor’s alleged leaks has offered important security lessons in how federal agents can access your devices if you have biometrics enabled. It also reveals at least one safeguard that can keep them out of those devices: Apple’s Lockdown mode for iOS. The feature, designed at least in part to prevent the hacking of iPhones by governments contracting with spyware companies like NSO Group, also kept the FBI out of Natanson’s phone, according to a court filing first reported by 404 Media. “Because the iPhone was in Lockdown mode, CART could not extract that device,” the filing read, using an acronym for the FBI’s Computer Analysis Response Team. That protection likely resulted from Lockdown mode’s security measure that prevents connection to peripherals—as well as forensic analysis devices like the Graykey or Cellebrite tools used for hacking phones—unless the phone is unlocked.
The role of Elon Musk and Starlink in the war in Ukraine has been complicated, and has not always favored Ukraine in its defense against Russia’s invasion. But Starlink this week gave Ukraine a significant win, disabling the Russian military’s use of Starlink, causing a communications blackout among many of its frontline forces. Russian military bloggers described the measure as a serious problem for Russian troops, in particular for its use of drones. The move reportedly comes after Ukraine’s defense minister wrote to Starlink’s parent company, SpaceX, last month. Now it appears to have responded to that request for help. “The enemy has not only a problem, the enemy has a catastrophe,” Serhiy Beskrestnov, one of the defense minister’s advisers, wrote on Facebook.
In a coordinated digital operation last year, US Cyber Command used digital weapons to disrupt Iran’s air missile defense systems during the US’s kinetic attack on Iran’s nuclear program. The disruption “helped to prevent Iran from launching surface-to-air missiles at American warplanes,” according to The Record. US agents reportedly used intelligence from the National Security Agency to find an advantageous weakness in Iran’s military systems that allowed them to get at the anti-missile defenses without having to directly attack and defeat Iran’s military digital defenses.
“US Cyber Command was proud to support Operation Midnight Hammer and is fully equipped to execute the orders of the commander-in-chief and the secretary of war at any time and in any place,” a command spokesperson said in a statement to The Record.
Tech
This Kit Turns Your Insta360 Action Camera Into a Point-and-Shoot

The final exposure control feature is one I use a lot, and it’s exposure compensation. This works with the auto exposure and can be used to combat the tendency to go too slow with the shutter speed be forcing the Ace Pro 2 to underexpose the image. The exposure comp here is the best among action cameras, running from –4 stops to + 4 stops in ⅓-stop increments. I set the Xplorer Grip to control EV, so when I am in auto mode, the dial is an exposure comp dial just like “real” camera. (The dial can also be set to control ISO, shutter speed, shooting mode, filter selection, and white balance.)
Even better, if you’re in manual mode and you want to go back to auto, the first click of the dial will open the side panel, the second will switch from manual to auto, the third will start adjusting your exposure value. This is a really fast way to get from a carefully composed exposure back to full auto without needing to get into the touchscreen menus.
The final thing worth mentioning is the included Leica color profiles. If you haven’t updated your firmware recently, you should. Insta360 has added a few more of these. Because I shoot RAW, I don’t use these much, but as color profiles go these are great, especially the new Leica high-contrast black and white, which is what I’ve been using most of the time. This way I get a black-and-white JPG and a full-color RAW file.
To be honest, I did not have high hopes for the Xplorer Grip Pro Kit. For me, action cameras have primarily been for shooting around water, and while that still works with the bare camera, it doesn’t with the grip. However, I was pleasantly surprised using the Ace Pro 2 with the Xplorer grip as an everyday camera.
I would say it’s best thought of as a compliment to your existing “real” camera. It’s not going to replace your interchangeable lens camera. It could replace your point-and-shoot, but I haven’t done that, because sometimes I want a pocket camera with a 28mm lens. Instead, the Ace Pro 2 with the grip has become an extra camera that I bring along when I want a wide angle or fisheye look and don’t feel like lugging a big, heavy, fast, full-frame, ultrawide lens.
Tech
ICE Agent’s ‘Dragging’ Case May Help Expose Evidence in Renee Good Shooting

Defense attorneys for a Minnesota man convicted in December of assaulting Immigration and Customs Enforcement officer Jonathan Ross are seeking access to investigative files related to the killing of Renee Nicole Good, after learning Ross was the same officer who shot and killed her during a targeted operation in Minneapolis last month.
Attorneys for Roberto Carlos Muñoz-Guatemala asked a federal judge on Friday to order prosecutors to turn over training records as well as investigative files related to Ross, the ICE agent who killed Good on January 7 during Operation Metro Surge and was also injured in a June 2025 incident in which Muñoz-Guatemala dragged him with his car.
A separate post-trial motion by the defense, filed in the US District Court in Minnesota, asks the judge to pause deadlines for a new-trial motion until the discovery motion is resolved.
Muñoz-Guatemala’s attorneys argue that even if the court ultimately decides that any newly discovered evidence doesn’t entitle their client to a new trial, he’s entitled to explore whether there are mitigating factors that could impact the length of his sentence, such as whether Ross’ injuries could have been, to some degree, brought upon him by his own behavior.
A jury convicted Muñoz-Guatemala on December 10 of assault on a federal officer with a dangerous weapon and causing bodily injury.
Court filings say that Ross and other agents were attempting to interview Muñoz-Guatemala last summer, and possibly process him for deportation, because he had an administrative warrant out for being in the country without authorization. They surrounded his Nissan Altima and attempted to remove him from the vehicle. Ross then used a tool to shatter the rear driver’s-side window before reaching inside. When the defendant accelerated away, Ross testified, he was dragged approximately 100 yards, during which time he repeatedly deployed a taser. Muñoz-Guatemala subsequently called 911 to report he’d been the victim of an assault.
During his trial, Muñoz-Guatemala said he didn’t understand that Ross—who according to his own testimony was wearing ranger green and gray and wore his badge on his belt—was a federal agent. (Ross testified that Muñoz-Guatemala had asked to speak to an attorney, which would suggest he knew Ross was acting as law enforcement, but an FBI agent who witnessed the incident said he didn’t hear this. According to court records, this claim did not come up in pretrial interviews, and prosecutors said they had not heard it before he made the claim in court.) Muñoz-Guatemala’s attorneys say now that had he been tried after Good’s killing, his defense may have also asserted that he was justified in resisting Ross, who they claim was the aggressor and used excessive force.
The argument is that the jury instructions essentially contained a two-part decision tree: Jurors could convict Muñoz-Guatemala if they believed he should have known Ross was law enforcement. They could also convict him if they believed driving away was not a reasonable response.
Muñoz-Guatemala’s conviction does not indicate which of these prongs the jury relied on. If it was the latter, the defense argues in the motion, the court should have access to evidence that may have bearing on Ross’ conduct, tactics, and whether he behaved aggressively—information that might indicate whether the agent has a history behaving recklessly in the field or contrary to his training.
Prosecutors have not yet filed a response to the motions. An email to an address associated with Ross in publicly available records did not result in an immediate response. The Department of Justice did not immediately respond to a request for comment. The Department of Homeland Security did not immediately respond to questions about Ross’ current duty status or the status of any departmental review.
Ross has been placed on administrative leave following the January 7 shooting of Good, a 37-year-old Minnesota poet and mother of three, a step DHS officials say is standard protocol after fatal use of force. Ross has not been charged in Good’s killing, and the Justice Department has said it will not pursue criminal charges.
-

 Tech6 days ago
Tech6 days agoHow to Watch the 2026 Winter Olympics
-

 Fashion1 week ago
Fashion1 week agoItaly’s Brunello Cucinelli debuts Callimacus AI e-commerce experience
-

 Business6 days ago
Business6 days agoPost-Budget Session: Bulls Push Sensex Up By Over 900 Points, Nifty Reclaims 25,000
-

 Tech1 week ago
Tech1 week agoRight-Wing Gun Enthusiasts and Extremists Are Working Overtime to Justify Alex Pretti’s Killing
-

 Fashion6 days ago
Fashion6 days agoCanada could lift GDP 7% by easing internal trade barriers
-

 Tech7 days ago
Tech7 days agoI Tested 10 Popular Date-Night Boxes With My Hinge Dates
-

 Business1 week ago
Business1 week agoVideo: Who Is Trump’s New Fed Chair Pick?
-

 Entertainment6 days ago
Entertainment6 days agoThe Traitors’ winner Rachel Duffy breaks heart with touching tribute to mum Anne

















