Tech
Heightened global risk pushes interest in data sovereignty | Computer Weekly

Heightened risk related to data sovereignty is universally acknowledged. Most IT decision makers see that risk increasing as a result of geopolitical instability, and that inadequate preparation could result in costly reputational damage and a loss of customer trust.
Those are the key findings of a Pure Storage-sponsored survey in which the University of Technology Sydney carried out interview-based qualitative research among IT practitioners in the Europe and Asia-Pacific regions.
The survey found:
- 100% of those asked believed sovereignty risks that include potential service disruption have forced organisations to reconsider where data is located;
- 92% said geopolitical shifts had increased sovereignty risks;
- 92% believed inadequate sovereignty planning could lead to reputational damage;
- 85% identified loss of customer trust as the key consequence of inaction;
- 78% said they had embraced data strategies that included engaging with multiple service providers; adopting sovereign datacentres (on-premise or in-country), and building enhanced governance requirements into commercial agreements.
The survey commentary talks of a “perfect storm” where service disruption risks, foreign influence and evolving regulations converge to create huge exposure to risk for organisations that could result in revenue loss, regulatory penalties and irreparable damage to stakeholder trust if not addressed.
One IT decision maker talked about how complex data sovereignty can be to unpick, and how it now forms key planks of their organisation’s agreements with customers.
“The Access Group handles sensitive end user data for our customers across the world, from the NHS in the UK to the Tax Department in Australia,” said Rolf Krolke, regional technology director for APAC with The Access Group. “Data sovereignty is an absolutely critical issue for us and our customers. In fact, they ask that it be written into our contracts.”
The concept of data sovereignty centres on the idea that information created, processed, converted and stored in digital form is subject to the laws of the country in which it was generated. But data can travel, too, and when it does, its destination country’s laws on data held there that must be adhered to. That is known as data residency.
Difficulties can arise when the two concepts meet and the laws of one state contradict another, such as with the European Union’s General Data Protection Regulation, which requires that data transferred to another jurisdiction is held with adequate safeguards and protections.
For such reasons, organisations often want to know where their data goes, and also might want to keep it in known – often home country – locations.
Such concerns have been heightened in the recent climate of geopolitical instability, as well as the febrile climate that has grown around international cyber crime.
The rise in use of the cloud is core to many of the concerns and the difficulties that arise.
Datacentre locations
Also present as concerns are datacentre locations and the global supply chain, said Patrick Smith, EMEA chief technology officer of Pure Storage, who suggests organisations and states will need to move to – or are already moving towards – building their own sovereign capacity.
This, he said, means physical equipment and in-country datacentre capacity, and that’s not a trivial obstacle to surmount.
“It’s interesting when you think about some of the constrained components that we’ve seen on the global stage,” said Smith. “A great example is Nvidia GPUs [graphics processing units], which require almost a global village to produce them.
“As soon as you start looking at data sovereignty, you’re looking at, ‘How do I build my sovereign capability? Where do I get all the components from?’ Many countries have effectively outsourced datacentres. They’ve put them outside of their own geography.
“With a sovereign capability, you’re talking about having to host those datacentres within your own borders,” he said. “And that suddenly means that you need to have that energy production and water supply to support that datacentre.”
Tech
The 11 Best Mattresses You Can Buy Online, Picked After Testing 100+

Compare Our Top Picks
Honorable Mentions
Photograph: Julia Forbes
We tested many mattresses last year and have already hit the ground running in 2026. That said, here are a few options we enjoyed and considered but ultimately didn’t make the starter team.
Sleep Number p6 Smart Bed for $3,199: This smart mattress offering from Sleep Number is designed to prioritize pressure relief in your sleep experience. If sensors detect areas that bear the brunt of your weight, “Responsive Air” chambers atop the p6 will adjust in real time to counteract it. It takes some getting used to to hear the bed inflate and deflate on its own, but it truly makes for a personalized sleep experience. Add built-in sleep tracking and 100 adjustable firmness levels, and you get a one-of-a-kind experience. However, to fully enjoy the mattress’s performance, it’s best to also get an adjustable base, which is a significant additional expense. —Julia Forbes. $3,199 to $7,998
Thuma Luxury Hybrid Mattress for $1,795: Thuma’s hybrid mattress is interesting because it blends together a smorgasbord of mattress materials: a Tencel cover, organic wool, memory foam, organic latex, and recycled-steel coils. The same rubberwood trees are used for Thuma’s popular Classic Bed frame, and for the Dunlop latex in this mattress. Of the three firmness levels offered—plush, medium, and firm—the medium was yielding some pretty strong support. The sleep trial is a bit unclear, as you only get 100 nights of coverage with your first Thuma purchase. So if you’ve already used it on a different Thuma product, like the frame, you may be out of luck here. —Julia Forbes. $1,295 to $1,995
Puffy Cloud for $949: This enhanced all-foam mattress offers profound pressure relief without feeling too soft, despite the name “Cloud” being in its name. The Puffy Cloud has a thinner profile and would most likely be too soft for bigger bodies. However, for lightweight and average builds, it really comes through to support the lower back and hug around pressure points. The thinness also didn’t compromise its motion isolation, which meant little to no shaking when my dogs jumped in and out of bed.—Julia Forbes. $449 to $1,298
The Saatva Contour5 for $2,999: The Contour5 is a newer offering from Saatva, replacing the popular Loom & Leaf in the company’s lineup. Like other Saatva mattresses, but unlike most others on this list, it is not roll-packed and comes delivered on a moving truck. The Contour5 has two firmness options and updated cooling tech that uses airflow channels in its gel foam layer, which is thinner than its predecessor, meaning it retains less heat. In my two weeks of testing, I found the Contour 5 was very good at remaining cool through summer nights, which is extra impressive given that it uses very dense 5-pound-weight memory foam. The Contour5 is soft enough for side sleeping without feeling like a saggy hammock and has excellent build quality, which is impressive for an all-foam mattress without springs. I prefer a hybrid with microcoils, but Saatva is popular for a reason, and as all-foam mattresses go, it has a true luxury feel. —Martin Cizmar. $1,899 to $3,599
The Big Fig Classic for $1,899: The Big Fig is designed for larger body frames. Being a bit overweight myself, I was eager to see how well this mattress, which is advertised as comfortably handling 550 pounds per sleeper, performed. It is a well-built mattress with an effective gel cooling layer; however, the aggressive edge support created a hammock-like feel despite the sturdy springs and three layers of high-density foam in the middle of the mattress. This was true both on my back and on my side. Others may appreciate the effect of sinking a bit into the center of the bed more than I do. —Martin Cizmar. $1,499 to $2,699
The Boring Hybrid Mattress for $799: Boring Mattress is a new company founded by two alums from Tuft & Needle. Simplicity is the company’s selling point. There is just one option: the Boring Hybrid Mattress. (You are allowed to pick a size.) This 10-inch hybrid has four layers of both foam and springs. I’m very sensitive to joint pain, and certain beds tend to make it worse, which is why pressure relief is super important for me. Having slept on a variety of different mattresses throughout the years, I was doubtful that this one would work. But I’ve slept on the hybrid mattress for months now and have yet to feel any pain at all. It strikes an excellent balance between firmness and support that my very particular self hasn’t been able to find with other options on the market. It’s worth noting, however, that its layers come equipped with an open-cell design that’s designed to move heat from your body while sleeping. I’m usually cold, so this feature isn’t that important to me. But on nights when I’ve cranked the heat up in my room and woken up sweating a bit, I can’t say it worked all that well for me. This isn’t a deal breaker, but I wouldn’t buy it solely for that. —Brenda Stolyar. $599 to $999
Casper The One for $799: Casper was a leader in the first wave of bed-in-a-box makers in 2014. The company has changed ownership and design a few times over the past decade but last year’s launch of The One finds the company keeping pace with competitors. This is an all-foam mattress that stands 11 inches tall. Because it’s all foam, it’s on the light side, with a queen weighing an easily movable 66 pounds. One of the main issues with all-foam beds is that they get too hot, but Casper’s The One uses an open-cell foam layer called Breathe Flex Foam on the top, which makes it both pleasantly squishy and breathable. Two more layers of foam add up to a medium-firm feel, with the middle layer designed to cradle your hips, and the base layer designed to provide support. —Martin Cizmar. $749 to $1,698
The Winkbed for $1,499: WIRED reviewer Julian Chokkattu slept on the luxury firm version of the WinkBed for almost two years and he was quite happy in that time. His favorite perk? The edge support is fantastic, so his partner never wakes when he slips into bed late at night. The plush pillowtop also adds a luxe, hotel-like feel to a relatively firm bed. —Martin Cizmar. $1,149 to $2,049
Silk and Snow S&S Organic for $1,000: I wouldn’t expect this to feel silky-soft, but the latex is supportive for sleep. I love how responsive (read: bouncy) this bed is, especially as someone who tosses and turns often. It’s able to move with me so I never feel unsupported, or overheated for that matter. Latex and coils are breathable, as are the organic cotton cover and wool fire barrier. —Julia Forbes. $800 to $1,300
Nest Bedding Quail for $1,299: When it comes to all-foam mattresses from classic bed-in-a-box brands, I prefer the Casper above, but the Quail by Nest is a nice option if you want an all-foam bed that’s a little firmer and you’re willing to pay a little more. My biggest issue with the Nest was that despite its claimed cooling system—the foam is infused with minerals and designed with an airflow layer—I did sleep a little hot on it during my week of testing. —Martin Cizmar. $849 to $1,499
Courtesy of Helix
Helix Sunset Elite for $3,749: Our top pick, Helix, also has an Elite collection that consists of seven mattresses along a spectrum of softness. At 15 inches high, the Sunset Elite is “the tallest mattress on the internet,” and comes shipped in two separate boxes, each heavy enough to max out FedEx requirements. The firmness is dictated by the foam density of the upper layer, which zips into a larger support system. This makes the mattress adjustable if you end up regretting your order. The bottom section has a separate layer of microcoils. I spent a month sleeping on the softest model from the Elite line, dubbed the Sunset, and appreciated the deep cradling effect. Helix offers a 100-day trial period on all of its mattresses. —Martin Cizmar. $2,499 to $4,499
DreamCloud Hybrid for $1,698: Don’t be turned off by that price just yet. This is one mattress that my husband begged me to keep, because the support and pressure relief set the bar so high. It’s been one of the most consistently performing mattresses I’ve tested over the years. And that seemingly high price? DreamCloud runs sales often, so expect to slash that in half. —Julia Forbes. $1,148 to $2,562
Wayfair Sleep 14-Inch Plush Cooling Gel Hybrid Mattress for $410: This plush mattress has a top layer of cooling gel that conforms to your body for comfort and has classic pocket coils below for structure and support, with layers of memory foams with varying thickness surrounding the coils for extra support (the coils and memory foam mixture helps with low motion transfer, too). The top knit cover and sides help with breathability and the overall cooling effect. The mattress is also compatible with an adjustable bed base, has solid edge support, is CertiPUR-US and Oeko-Tex Certified (ensuring no harmful toxins), and has a 10-year warranty. This bed is super comfy if you like a more plush mattress. —Molly Higgins. $400 to $700
Mattresses to Avoid
Not every mattress we test can be a winner, which is why we test in the first place. Here are a few that did not make the cut according to our standards.
Birch Elite Hybrid for $3,749: This is the newest model from Birch, and frankly, you would be just fine sticking with the Birch Natural or Birch Luxe Natural instead. The Birch Elite Hybrid was incredibly top-heavy and incredibly difficult to move, given the floppiness and weight of its numerous latex and coil layers. The top layers slid around, creating a lumpy surface, and the new “CoolForce” layer was completely undetectable. —Julia Forbes. $2,499 to $4,499
Brooklyn Bedding Spartan for $1,099: This mattress is designed for “athletic recovery,” and as a former collegiate athlete, I was excited to try it. I had opted for medium firmness over the soft and firm options, but upon receiving it, I had to double-check that I hadn’t gotten the soft option by accident. The medium cratered around me, leaving me with unhappy pressure points. The lack of overall support didn’t help me recover from soreness, so I couldn’t tell you whether the Far Infrared Ray recovery tech in the cover helped at all. —Julia Forbes $1,099 to $2,399
Sleep Number Climate360 Smart Bed for $10,249: This bed can be temperature-controlled, which is amazing. The adjustable base means you can be comfortable when watching TV, reading, or sleeping. Unfortunately, the price tag has too many digits, and sleep experts recommend avoiding electronic usage before bed—advice the Sleep IQ app defies. Did we mention it costs as much as a used Buick and the weight is not far behind? —Martin Cizmar. $10,249 to $14,499
Tempur-Pedic Tempur-Adapt for $2,199: Tempur-Pedic is one of the country’s best-known and loved mattress brands, but two separate WIRED reviewers (Martin Cizmar and Nena Farrell) have both disliked different mattresses from the company over the past two years. Nena found the Tempur-Adapt totally lacking in support, and felt like she was sinking into a void when she lay on it. Her spine and muscles both ached after sleeping on it so she gave it to her sister who also hated it, describing it as like sleeping on a leaky air mattress. —Martin Cizmar. $1,699 to $3,398
Amazon Basics mattress for $170 (Twin): This one is made of cheap foam that isn’t dense enough, causing too much sinkage. —Martin Cizmar. $170 to $436
Parachute Eco Comfort Mattress for $2,650: This mattress just doesn’t live up to its extravagant price. The model we tested didn’t have enough proper padding above its coils. —Martin Cizmar. $1,550 to $2,850
Frequently Asked Questions
Our testing process is simple—we dedicate a week or so to each mattress, sleeping on it at home to understand what it’s all about. The WIRED Reviews testing team has been refining our testing methodology since 2019, when we would try out mattresses side by side in a conference room, much like a mattress store experience. But just like what can happen at a mattress store, the experiences we were documenting in these brief observations could change the more time we spent with a mattress. Hence, we went back to basics and dedicated a week or more to sleeping on each one, noting down our nightly experiences.
That being said, I have spent the last six years as a certified sleep science coach and professional mattress testing becoming a mattress sommelier of sorts. Instead of devising tests to show how much a bed can support at the edge or reduce motion transfer, it really comes down to understanding the range of materials, sleeping positions, and body types in the mattress space.
What Should You Look for When Buying a Mattress?
Mattress shopping requires a bit of self-assessment before you even get into the particulars of a mattress. Taking note of your body type, preferred sleeping position, pain points, and material preferences for things like allergies or staying chemical-free are all data points that make the search a lot easier. From there, we can help you narrow down options for different scenarios, such as if you are a couple looking for a firm mattress to help with back pain. For that, I’d point you to some of our other guides, such as the best mattresses for sex and the best mattresses for back pain, to discuss some of our favorite options we’ve tested.
What Are Mattress Certifications?
This is one of the most critical factors to look for when buying a mattress, as it’s basically a cheat code for evaluating a mattress’s material and quality claims. For mattresses that use memory foam or organic and natural components, mattress certifications help us, as consumers, gain insight into the sourcing and safety of these materials. CertiPUR-US certification is a non-negotiable for me when it comes to memory foam because it shows that harmful chemicals were not used in its production. GreenGuard Gold is another certification that ensures any off-gassing from your mattress upon unboxing won’t affect your indoor air quality—important if you have sensitive skin, a strong sense of smell, allergies, or asthma.
How Long Does a Mattress Last?
As a ballpark estimate, your mattress should last eight to 10 years. I don’t recommend going much beyond that, as the mattress materials are past their prime and aren’t providing adequate support or comfort.
Just like picking out a bed, there are several factors involved that dictate how long it’ll last. Durability of the mattress’s materials always comes into play, as beds with coils tend to remain more structurally intact than all-foam beds, which can sag around the middle and edges over time. Your build also plays into this, because if your bed starts to buckle under your weight night after night, that’s obviously an issue. If this is the case for you, I’d recommend reviewing your warranty to see if it can be replaced.
How Long of a Mattress Warranty Should I Look For?
The industry standard for a warranty is about 10 years, so that should be the minimum in most cases. Many brands will offer prorated coverage beyond that decade mark, meaning the mattress can be replaced at a significant discount, depending on how long it’s been. This is where the fine print of a warranty is especially important to review, because many mattresses offer lifetime warranties. For example, DreamCloud has a “Forever Warranty” that fully covers its mattresses the first 10 years. After that 10-year mark, you have to pay $50 each way for the mattress repair or replacement to be delivered. It’s still a good deal, but something to be aware of.
Should I Buy My Mattress In-Store or Online?
Where you purchase your mattress is another personal preference. Many people may live near a showroom that sells a mattress they’ve been eyeballing, and want to go see it in person before buying. Others may do that and wait for an online holiday sale to secure a major deal.
The nice thing about buying online is that you get much more variety than what you’d get with a mattress store. You’ll still receive the sleep trial component that most brands offer for in-store purchases when opting to do so online. You can try the bed from the comfort of your home for a set number of days, typically 90 nights to an entire year, depending on the brand. Many companies, but not all, will require a 30-day adjustment period for you to get used to the mattress before they will process a return. If you do end up returning a mattress, some brands, both online and brick-and-mortar, may ask you to donate it to a local charity or arrange for pickup as part of the warranty. By donating, mattresses are kept out of landfills and put to good use.
Should I Wait for a Mattress Sale Before I Buy?
In all honesty, it comes down to how you’re currently faring with your mattress and sleep schedule. If you’re sleep-deprived and ready for a change, there’s no time like the present. We do cover coupons and promos that come up in non-holiday periods. For example, we have a special code for the Nolah Evolution running at all times.
During the holidays, the WIRED Reviews process is unique because we meticulously track price changes and sales year-round. That way, we can deliver news about the really good sales rather than what’s dominating headlines. Major mattress sales weekends include Presidents’ Day, Memorial Day, Fourth of July, Labor Day, Black Friday, and Cyber Monday. There are plenty of ad hoc sales that pop up for various events in between, too.
How Does WIRED Acquire Mattresses for Testing?
We conduct a lot of research about what’s new in the mattress world, as well as the legacy of established brands and models. To perform hands-on testing, we will request free media samples from these brands or buy them outright on sites like Amazon or Wayfair, or from smaller vendors. Some brands will engage with us in partnerships, but that does not dictate their placement within an article, what we say about the product, or even if we cover it. Even if we receive commission, it’s essential that we publish our true account of our experiences.
What Does WIRED Do With the Mattresses After Testing Them?
Because most mattresses we test are provided as media samples, we donate them locally upon completion of testing.
Power up with unlimited access to WIRED. Get best-in-class reporting and exclusive subscriber content that’s too important to ignore. Subscribe Today.
Tech
Virgin Media O2 accelerates automation across mobile network | Computer Weekly

Virgin Media O2 (VMO2) is deploying artificial intelligence (AI) monitoring tools in its mobile network to predict and prevent network issues, helping to deliver a more reliable and consistent experience for customers across the UK.
In its strategy to maintain acceptable performance levels for mobile users, VMO2 has expanded its relationship with infrastructure modernisation firm Zinkworks. VMO2) added that it is building on two years of experience monitoring its fixed broadband network, where the technology is said to have reduced repair times by more than a third, cutting the need for engineer visits by 12%.
The operator is extending this approach into its mobile network, deploying AI-driven automation technology to minimise downtime across its mobile network, as well as to pre-empt issues and maximise network uptime.
The expanded partnership with Zinkworks will aim to support more resilient and reliable mobile connectivity across the UK, improving performance during peak demand and delivering a more consistent customer experience. It will focus on monitoring network performance, identifying patterns and behaviours, detecting and resolving issues faster, and anticipating faults before they escalate into service issues. The firm said it will strive to improve performance during periods of high demand and allow operational decisions to be made before customers are even affected.
The initiative is based on the core Google Cloud platform and features such as Gemini and Vertex AI to deliver AI-enabled autonomous network capabilities for Virgin Media O2. The management technology will be deployed across key parts of the VMO2 mobile network, including radio access, core systems and network operations. By combining real-time network data with intelligent automation, the network can continuously monitor itself, anticipate potential problems and take corrective action, with engineers retaining complete oversight.
Virgin Media O2 said that the new project supports its continued work to transform and evolve its networks as it moves toward more autonomous network operations, enabling greater resilience and performance as customer demand continues to grow.
“At Virgin Media O2, we are investing every single day to improve our mobile network and provide a more reliable experience for our customers,” said Jeanie York, CTO at Virgin Media O2. “Greater automation will help us to predict and prevent issues and allow us to better spot and fix problems when they arise, reducing downtime and ensuring customers can trust us to deliver the dependable mobile experience they rely on.”
Zinkworks CEO Paul Madden added: “Mobile operators globally are looking for ways to harness AI at scale, and Virgin Media O2 is at the forefront of this shift. By combining Virgin Media O2’s ambition and our engineering expertise, we are building capabilities that will reduce outages, improve performance and deliver tangible benefits to customers across the UK.”
The project with VMO2 comes after Zinkworks signed a partnership with Vodafone in October 2025 to develop a generative AI-driven platform intended to improve mobile service quality, network energy efficiency and performance for Vodafone customers throughout Europe.
The central platform, called Rapid RIC, is expected to be fully operational by early 2026. It will combine Vodafone’s data analytics, a visual interface and code-generating AI to enable engineers in multiple markets to more easily develop, deploy and monitor RAN automation rApps, which are innovative applications that empower the evolution and healing of networks.
Tech
Two Titanic Structures Hidden Deep Within the Earth Have Altered the Magnetic Field for Millions of Years
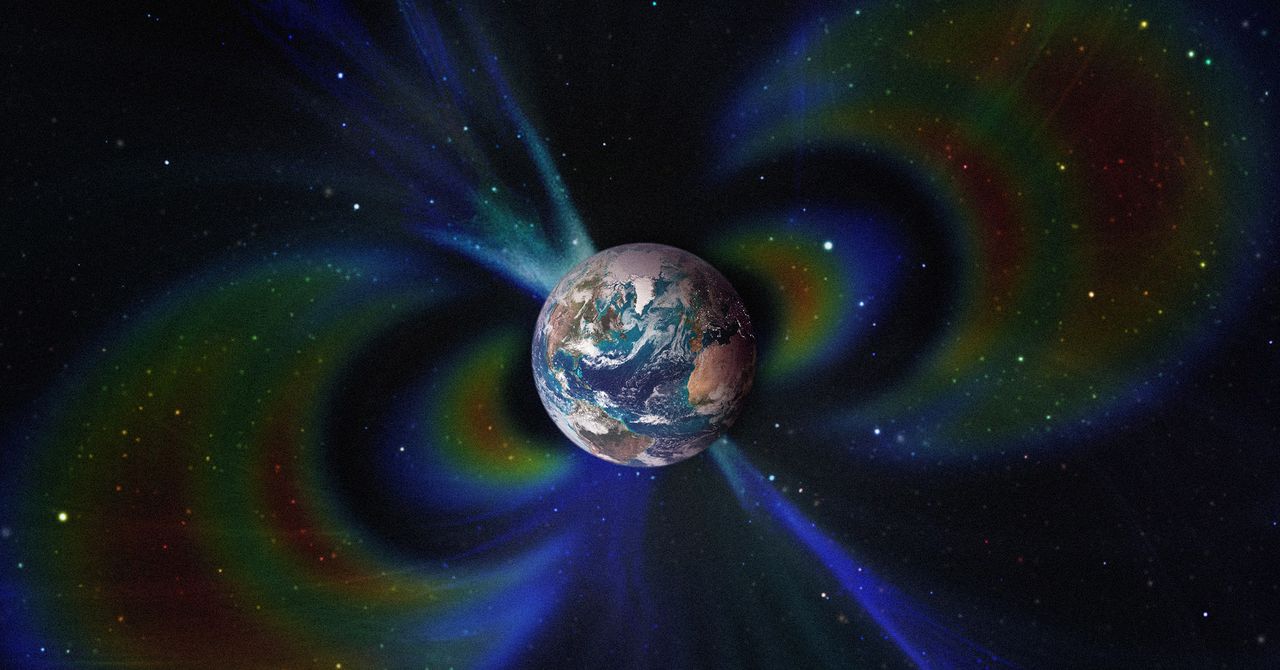
A team of geologists has found for the first time evidence that two ancient, continent-sized, ultrahot structures hidden beneath the Earth have shaped the planet’s magnetic field for the past 265 million years.
These two masses, known as large low-shear-velocity provinces (LLSVPs), are part of the catalog of the planet’s most enormous and enigmatic objects. Current estimates calculate that each one is comparable in size to the African continent, although they remain buried at a depth of 2,900 kilometers.
Low-lying surface vertical velocity (LLVV) regions form irregular areas of the Earth’s mantle, not defined blocks of rock or metal as one might imagine. Within them, the mantle material is hotter, denser, and chemically different from the surrounding material. They are also notable because a “ring” of cooler material surrounds them, where seismic waves travel faster.
Geologists had suspected these anomalies existed since the late 1970s and were able to confirm them two decades later. After another 10 years of research, they now point to them directly as structures capable of modifying Earth’s magnetic field.
LLSVPs Alter the Behavior of the Nucleus
According to a study published this week in Nature Geoscience and led by researchers at the University of Liverpool, temperature differences between LLSVPs and the surrounding mantle material alter the way liquid iron flows in the core. This movement of iron is responsible for generating Earth’s magnetic field.
Taken together, the cold and ultrahot zones of the mantle accelerate or slow the flow of liquid iron depending on the region, creating an asymmetry. This inequality contributes to the magnetic field taking on the irregular shape we observe today.
The team analyzed the available mantle evidence and ran simulations on supercomputers. They compared how the magnetic field should look if the mantle were uniform versus how it behaves when it includes these heterogeneous regions with structures. They then contrasted both scenarios with real magnetic field data. Only the model that incorporated the LLSVPs reproduced the same irregularities, tilts, and patterns that are currently observed.
The geodynamo simulations also revealed that some parts of the magnetic field have remained relatively stable for hundreds of millions of years, while others have changed remarkably.
“These findings also have important implications for questions surrounding ancient continental configurations—such as the formation and breakup of Pangaea—and may help resolve long-standing uncertainties in ancient climate, paleobiology, and the formation of natural resources,” said Andy Biggin, first author of the study and professor of Geomagnetism at the University of Liverpool, in a press release.
“These areas have assumed that Earth’s magnetic field, when averaged over long periods, behaved as a perfect bar magnet aligned with the planet’s rotational axis. Our findings are that this may not quite be true,” he added.
This story originally appeared in WIRED en Español and has been translated from Spanish.
-

 Business1 week ago
Business1 week agoPSX witnesses 6,000-point on Middle East tensions | The Express Tribune
-

 Tech1 week ago
Tech1 week agoThe Surface Laptop Is $400 Off
-

 Tech1 week ago
Tech1 week agoHere’s the Company That Sold DHS ICE’s Notorious Face Recognition App
-

 Tech4 days ago
Tech4 days agoHow to Watch the 2026 Winter Olympics
-

 Tech7 days ago
Tech7 days agoRight-Wing Gun Enthusiasts and Extremists Are Working Overtime to Justify Alex Pretti’s Killing
-

 Entertainment1 week ago
Entertainment1 week agoPeyton List talks new season of "School Spirits" and performing in off-Broadway hit musical
-

 Business1 week ago
Business1 week agoBudget 2026: Defence, critical minerals and infra may get major boost
-

 Sports1 week ago
Sports1 week agoDarian Mensah, Duke settle; QB commits to Miami


%2520(1).png)




