Tech
How to See WIRED in Your Google Searches

As you’ve probably noticed, Google has gotten … weird lately. Weirder? It can be hard to find the search results you’re looking for. Between AI summaries and algorithm changes resulting in unexpected sources, it can be tricky to navigate the most popular search engine in the world. (And publishers are feeling the strain, too.)
Earlier this year, Google updated its algorithm. This is nothing new—Google updates its algorithms hundreds of times per year, with anywhere from two to four major “core updates” that result in significant changes. And while it’s tricky to determine exactly what changed, publishers and websites large and small noticed significant traffic drops and lower search rankings—even for content that had previously been doing well. “Google Zero” (as Nilay Patel of The Verge first called it) is thought to be caused, at least in part, by AI overviews.
Google Search has shown a slow crawl toward this for a couple of years, but the most recent blow was delivered over the summer. When you search for something and you get a neat little summary of various reporting completed by journalists, you’re less likely to visit the websites that actually did the work. And, in some instances, that summary contains incorrect AI hallucinations or reporting from websites you might not trust as much. It’s hard to say whether the next core update will make your search results show what you expect, but in the meantime, there’s a tweak that can help it feel more tailored to your preferences.
Take back control of your Google search results with the new Google “Preferred Sources” tool. This can help you see more of WIRED, from our rigorous and obsessive Reviews coverage to the important breaking stories on our Politics desk to our Culture team’s “What to Watch” roundups. (And, yes, this works for other publishers you know and trust, too.)
Preferred Sources are prioritized in Top Stories search results, and you’ll also get a dedicated From Your Sources section on some search results pages.
To set WIRED as a Preferred Source, you can click this link and check the box to the right. You can also search for additional sources you prefer on this page and check the respective boxes to make sure they’re prioritized in your Google searches.
Google via Louryn Strampe
Tech
Onnit’s Instant Melatonin Spray Is the Easiest Part of My Nightly Routine

I’ve always approached taking melatonin supplements with skepticism. They seem to help every once in a while, but your brain is already making melatonin. Beyond that, I am not a fan of the sickly-sweet tablets, gummies, and other forms of melatonin I’ve come across. No one wants a bad taste in their mouth when they’re supposed to be drifting off to sleep.
This is where Onnit’s Instant Melatonin Spray comes in. Fellow WIRED reviewer Molly Higgins first gave it a go, and reported back favorably. This spray comes in two flavors, lavender and mint, and is sweetened with stevia. While I wouldn’t consider it a gourmet taste, I appreciate that it leans more into herbal components known for sleep and relaxation.
Keep in mind that melatonin is meant to be a sleep aid, not a cure-all. That being said, one serving of this spray has 3 milligrams of melatonin, which takes about six pumps to dispense. While 3 milligrams may not seem like a lot to really kickstart your circadian rhythm, it’s actually the ideal dosage to get your brain’s wind-down process kicked off. Some people can do more (but don’t go over 10 milligrams!), some less, but based on what experts have relayed to me, this is the preferable amount.
A couple of reminders for any supplement: consult your doctor if and when you want to incorporate anything, melatonin included, into your nighttime regimen. Your healthcare provider can help confirm that you’re not on any medications where adding a sleep aid or supplement wouldn’t feel as effective. Onnit’s Instant Melatonin Spray is International Genetically Modified Organism Evaluation and Notification certified (IGEN) to verify that it uses truly non-GMO ingredients.
Apart from that, there may be some trial and error on the ideal amount for you, and how much time it takes to kick in. Some may feel the melatonin sooner than others. For my colleague Molly, it took about an hour. Melatonin can’t do all the heavy lifting, so make sure you’re ready to go to bed when you take it, and that your sleep space is set up for sleep success, down to your mattress, sheets, and pillows.
Tech
I Tested Bosch’s New Vacuum Against Shark and Dyson. It Didn’t Beat Them
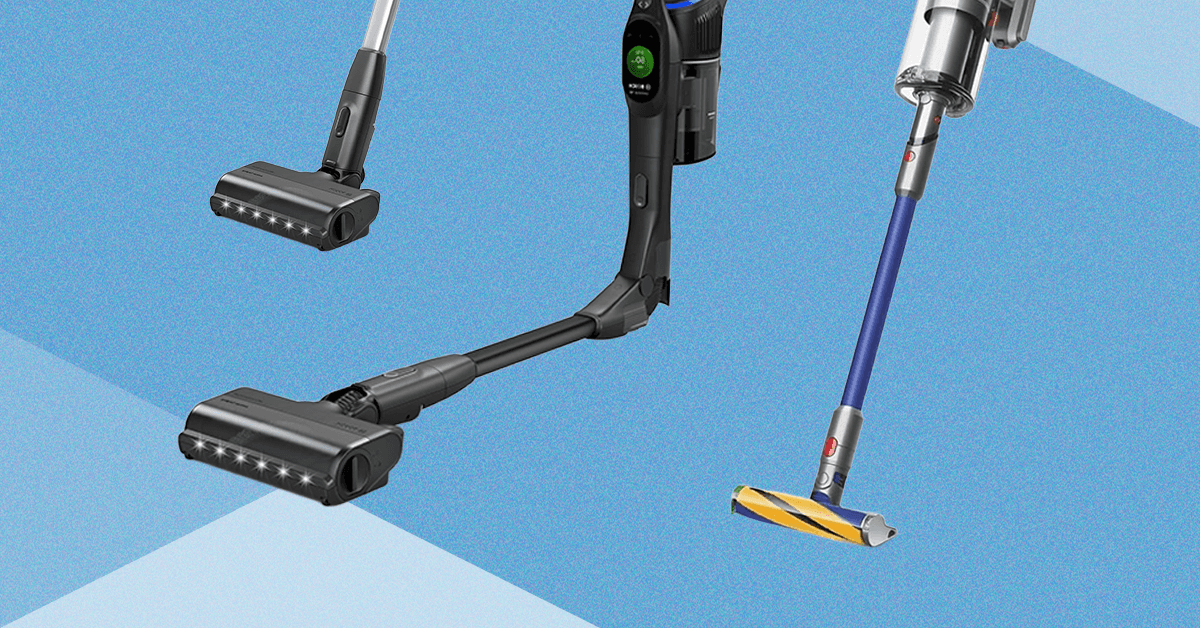
There’s a lever on the back for this compression mechanism that you manually press down and a separate button to open the dustbin at the bottom. You can use the compression lever when it’s both closed and open. It did help compress the hair and dust while I was vacuuming, helping me see if I had really filled the bin, though at a certain point it doesn’t compress much more. It was helpful to push debris out if needed too, versus the times I’ve had to stick my hand in both the Dyson and Shark to get the stuck hair and dust out. Dyson has this same feature on the Piston Animal V16, which is due out this year, so I’ll be curious to see which mechanism is better engineered.
Bendable Winner: Shark
Photograph: Nena Farrell
If you’re looking for a vacuum that can bend to reach under furniture, I prefer the Shark to the Bosch. Both have a similar mechanism and feel, but the Bosch tended to push debris around when I was using it with an active bend, while the Shark managed to vacuum up debris I couldn’t get with the Bosch without lifting it and placing it on top of that particular debris (in this case, rogue cat kibble).
Accessory Winner: Dyson
Dyson pulls ahead because the Dyson Gen5 Detect comes with three attachments and two heads. You’ll get a Motorbar head, a Fluffy Optic head, a hair tool, a combination tool, and a dusting and crevice tool that’s actually built into the stick tube. I love that it’s built into the vacuum so that it’s one less separate attachment to carry around, and it makes me more likely to use it.
But Bosch does well in this area, too. You’ll get an upholstery nozzle, a furniture brush, and a crevice nozzle. It’s one more attachment than you’ll get with Shark, and Bosch also includes a wall mount that you can wire the charging cord into for storage and charging, and you can mount two attachments on it. But I will say, I like that Shark includes a simple tote bag to store the attachments in. The rest of my attachments are in plastic bags for each vacuum, and keeping track of attachments is the most annoying part of a cordless vacuum.
Build Winner: Tie
Photograph: Nena Farrell
All three of these vacuums have a good build quality, but each one feels like it focuses on something different. Bosch feels the lightest of the three and stands up the easiest on its own, but all three do need something to lean against to stay upright. The Dyson is the worst at this; it also needs a ledge or table wedged under the canister, or it’ll roll forward and tip over. The Bosch has a sleek black look and a colorful LED screen that will show you a picture of carpet or hardwood depending on what mode it’s vacuuming in. The vacuum head itself feels like the lightest plastic of the bunch, though.
Tech
Right-Wing Gun Enthusiasts and Extremists Are Working Overtime to Justify Alex Pretti’s Killing

Brandon Herrera, a prominent gun influencer with over 4 million followers on YouTube, said in a video posted this week that while it was unfortunate that Pretti died, ultimately the fault was his own.
“Pretti didn’t deserve to die, but it also wasn’t just a baseless execution,” Herrera said, adding without evidence that Pretti’s purpose was to disrupt ICE operations. “If you’re interfering with arrests and things like that, that’s a crime. If you get in the fucking officer’s way, that will probably be escalated to physical force, whether it’s arresting you or just getting you the fuck out of the way, which then can lead to a tussle, which, if you’re armed, can lead to a fatal shooting.” He described the situation as “lawful but awful.”
Herrera was joined in the video by former police officer and fellow gun influencer Cody Garrett, known online as Donut Operator.
Both men took the opportunity to deride immigrants, with Herrera saying “every news outlet is going to jump onto this because it’s current thing and they’re going to ignore the 12 drunk drivers who killed you know, American citizens yesterday that were all illegals or H-1Bs or whatever.”
Herrera also referenced his “friend” Kyle Rittenhouse, who has become central to much of the debate about the shooting.
On August 25, 2020, Rittenhouse, who was 17 at the time, traveled from his home in Illinois to a protest in Kenosha, Wisconsin, brandishing an AR-15-style rifle, claiming he was there to protect local businesses. He killed two people and shot another in the arm that night.
Critics of ICE’s actions in Minneapolis quickly highlighted what they saw as the hypocrisy of the right’s defense of Rittenhouse and attacks on Pretti.
“Kyle Rittenhouse was a conservative hero for walking into a protest actually brandishing a weapon, but this guy who had a legal permit to carry and already had had his gun removed is to some people an instigator, when he was actually going to help a woman,” Jessica Tarlov, a Democratic strategist, said on Fox News this week.
Rittenhouse also waded into the debate, writing on X: “The correct way to approach law enforcement when armed,” above a picture of himself with his hands up in front of police after he killed two people. He added in another post that “ICE messed up.”
The claim that Pretti was to blame was repeated in private Facebook groups run by armed militias, according to data shared with WIRED by the Tech Transparency Project, as well as on extremist Telegram channels.
“I’m sorry for him and his family,” one member of a Facebook group called American Patriots wrote. “My question though, why did he go to these riots armed with a gun and extra magazines if he wasn’t planning on using them?”
Some extremist groups, such as the far-right Boogaloo movement, have been highly critical of the administration’s comments on being armed at a protest.
“To the ‘dont bring a gun to a protest’ crowd, fuck you,” one member of a private Boogaloo group wrote on Facebook this week. “To the fucking turn coats thinking disarming is the answer and dont think it would happen to you as well, fuck you. To the federal government who I’ve watched murder citizens just for saying no to them, fuck you. Shall not be infringed.”
-

 Business1 week ago
Business1 week agoSuccess Story: This IITian Failed 17 Times Before Building A ₹40,000 Crore Giant
-

 Fashion1 week ago
Fashion1 week agoSouth Korea tilts sourcing towards China as apparel imports shift
-

 Sports1 week ago
Sports1 week agoTransfer rumors, news: Saudi league eyes Salah, Vinícius Jr. plus 50 more
-

 Sports5 days ago
Sports5 days agoPSL 11: Local players’ category renewals unveiled ahead of auction
-

 Entertainment1 week ago
Entertainment1 week agoThree dead after suicide blast targets peace committee leader’s home in DI Khan
-

 Sports1 week ago
Sports1 week agoWanted Olympian-turned-fugitive Ryan Wedding in custody, sources say
-

 Tech1 week ago
Tech1 week agoStrap One of Our Favorite Action Cameras to Your Helmet or a Floaty
-

 Tech1 week ago
Tech1 week agoThis Mega Snowstorm Will Be a Test for the US Supply Chain