Tech
Oracle patches E-Business suite targeted by Cl0p ransomware | Computer Weekly
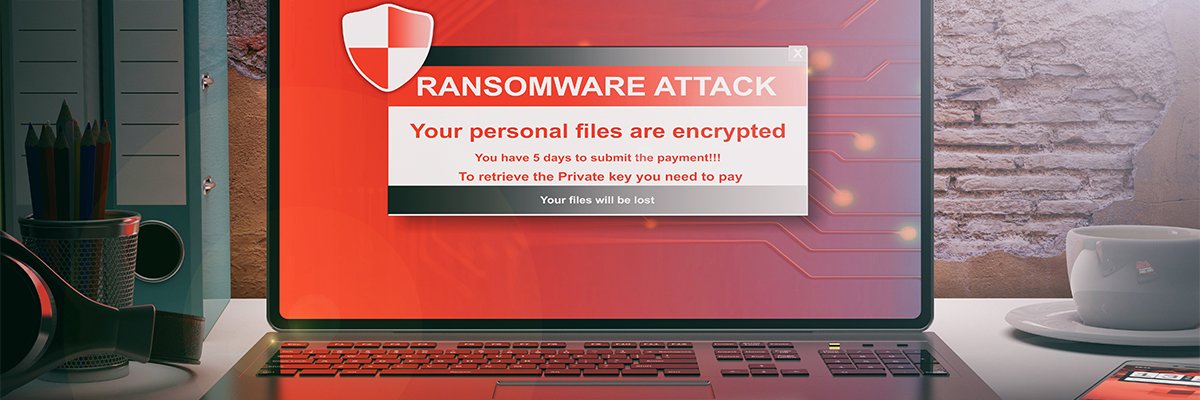
Oracle has issued a fix for a critical remote code execution (RCE) vulnerability in its E-Business Suite (EBS) as the well-used ERP software package emerges as the latest vector for mass Cl0p (aka Clop) ransomware attacks.
The Oracle EBS ecosystem is deeply embedded in enterprise financial and operational systems, which offers hackers access to a wide range of high-value targets and potentially extreme impacts.
The flaw in question, CVE-20225-61882, is present in versions 1.2.2.3 through 12.2.14 of EEBS, and affects a concurrent task processing component that enables users to run multiple processes simultaneously.
Rated 9.8 on the CVSS scale, it is considered relatively easy to take advantage of. Importantly, an unauthenticated attacker can exploit it over the network without any user interaction needed, leading to RCE.
Oracle EBS ecosystem, often deeply embedded in financial and operational systems, offers high-value targets with far-reaching business impact
“Oracle always recommends that customers remain on actively-supported versions and apply all Security Alerts and Critical Patch Update security patches without delay.
“Note that the October 2023 Critical Patch Update is a prerequisite for application of the updates in this Security Alert,” the supplier added.
In its advisory notice Oracle shared a number of indicators of compromise (IoCs) that appeared to link exploitation of CVE-2025-61882 to both the Cl0p ransomware crew and the Scattered Lapsus$ Hunters collective – which is not necessarily implausible as Scattered Spider has been known to act as a ransomware affiliate in the past.
Jake Knott, principal security researcher at watchTowr, said that exploitation of EBS appeared to date back to August 2025, and warned that as of Monday 6 October, exploit code for CVE-2025-61882 was publicly available.
“At first glance, it looked reasonably complex and required real effort to reproduce manually. But now, with working exploit code leaked, that barrier to entry is gone. It’s likely that almost no one patched over the weekend. So we’re waking up to a critical vulnerability with public exploit code and unpatched systems everywhere,” said Knott.
“We fully expect to see mass, indiscriminate exploitation from multiple groups within days. If you run Oracle EBS, this is your red alert. Patch immediately, hunt aggressively, and tighten your controls, fast.”
Writing on LinkedIn, Charles Carmakal, chief technical officer and board advisor at Google Cloud’s Mandiant, confirmed this, saying that Cl0p had almost certainly exploited multiple other EBS vulnerabilities – including some that were patched a couple of months ago – as well. The gang has supposedly been contacting victims since early last week, but Carmakal added that it may have not made contact with all of them just yet.
Cl0p’s warning from history
As seen in 2023, when it successfully targeted a flaw in Progress Software’s MOVEit managed file transfer (MFT) software product to extort potentially hundreds of victims, the Cl0p gang makes a habit of conducting mass exploitation activities against multiple downstream organisations through widely-used software packages. The mass targeting of Oracle EBS now being seen does fit this established modus operandi.
Historically, Cl0p’s activity comes in short, high-profile bursts in-between lengthy periods of downtime – likely due to the administrative burden its mass-attacks create – and Kroll managing director of cyber and data resilience, Max Henderson, had been among those warning for some weeks that the gang looked likely to resurface. He told Computer Weekly that others may follow, and described “grim” impacts.
“There should be an urgent rush for victims and users of Oracle to patch this, as continued attacks or attacks from other groups may continue. We expect a long tail of self-identifying victims with this situation, as many victims are unaware of extortion emails sitting in their junk folders,” said Henderson.
Tech
Lenovo’s Latest Wacky Concepts Include a Laptop With a Built-In Portable Monitor

Do you like having a second screen with your computer setup? What if your laptop could carry a second screen for you? That’s the idea behind Lenovo’s latest proof of concept, the ThinkBook Modular AI PC, announced at Mobile World Congress in Barcelona.
Lenovo is never shy to show off wacky, weird concept laptops. We’ve seen a PC with a transparent screen, one with a rollable OLED screen, a swiveling screen, and another with a flippy screen. At CES earlier this year, the company showed off a gaming laptop with a display that expands at the push of a button. Sometimes, these concepts turn into real products that go on sale (often in limited quantities).
At MWC 2026, Lenovo trotted out three concepts. While it’s unclear whether any of them will become real, purchasable products, there’s some unique utility here, and a peek at how computing experiences could change in the future.
A Laptop With a Built-In Portable Screen
As someone with a multi-screen setup at home and a fondness for portable monitors, the ThinkBook Modular AI PC appeals to me the most. At first glance, it looks like a normal laptop. Take a look behind, and you’ll notice there’s a second screen magnetically hanging off the back of the laptop, like a koala carrying a baby on its back.
The screen is connected to the laptop using pogo-pin connectors, so you can use it in this state to display content to people in front of you, say, if you were making a presentation during a meeting. Alternatively, you can pop this second screen off, remove a hidden kickstand resting under the laptop, and magnetically attach it to the 14-inch screen so that you have a traditional portable monitor experience. (You’ll need to connect this to the laptop via a USB-C cable in this orientation.)
If you don’t have the desk space for that orientation, you can always remove the keyboard from the base and pop the second screen there—it’ll auto-connect to the laptop via the pogo pins, and you’ll be able to use the Bluetooth keyboard to type on a dual-screen setup that resembles the Asus ZenBook Duo. The whole system is a fantastically portable method of improving productivity on the go, and the laptop isn’t too thick or cumbersome.
Tech
The 5 Big ‘Known Unknowns’ of Donald Trump’s New War With Iran

More recently, Iran has been a regular adversary in cyberspace—and while it hasn’t demonstrated quite the acuity of Russia or China, Iran is “good at finding ways to maximize the impact of their capabilities,” says Jeff Greene, the former executive assistant director of cybersecurity at CISA. Iran, in particular, famously was responsible for a series of distributed-denial-of-service attacks on Wall Street institutions that worried financial markets, and its 2012 attack on Saudi Aramco and Qatar’s Rasgas marked some of the earliest destructive infrastructure cyberattacks.
Today, surely, Iran is weighing which of these tools, networks, and operatives it might press into a response—and where, exactly, that response might come. Given its history of terror campaigns and cyberattacks, there’s no reason to think that Iran’s retaliatory options are limited to missiles alone—or even to the Middle East at all.
Which leads to the biggest known unknown of all:
5. How does this end? There’s an apocryphal story about a 1970s conversation between Henry Kissinger and a Chinese leader—it’s told variously as either Mao-Tse Tung or Zhou Enlai. Asked about the legacy of the French revolution, the Chinese leader quipped, “Too soon to tell.” The story almost surely didn’t happen, but it’s useful in speaking to a larger truth particularly in societies as old as the 2,500-year-old Persian empire: History has a long tail.
As much as Trump (and the world) might hope that democracy breaks out in Iran this spring, the CIA’s official assessment in February was that if Khamenei was killed, he would be likely replaced with hardline figures from the Islamic Revolutionary Guard Corps. And indeed, the fact that Iran’s retaliatory strikes against other targets in the Middle East continued throughout Saturday, even after the death of many senior regime officials—including, purportedly, the defense minister—belied the hope that the government was close to collapse.
The post-World War II history of Iran has surely hinged on three moments and its intersections with American foreign policy—the 1953 CIA coup, the 1979 revolution that removed the shah, and now the 2026 US attacks that have killed its supreme leader. In his recent bestselling book King of Kings, on the fall of the shah, longtime foreign correspondent Scott Anderson writes of 1979, “If one were to make a list of that small handful of revolutions that spurred change on a truly global scale in the modern era, that caused a paradigm shift in the way the world works, to the American, French, and Russian Revolutions might be added the Iranian.”
It is hard not to think today that we are living through a moment equally important in ways that we cannot yet fathom or imagine—and that we should be especially wary of any premature celebration or declarations of success given just how far-reaching Iran’s past turmoils have been.
Defense Secretary Pete Hegseth has repeatedly bragged about how he sees the military and Trump administration’s foreign policy as sending a message to America’s adversaries: “F-A-F-O,” playing off the vulgar colloquialism. Now, though, it’s the US doing the “F-A” portion in the skies over Iran—and the long arc of Iran’s history tells us that we’re a long, long way from the “F-O” part where we understand the consequences.
Let us know what you think about this article. Submit a letter to the editor at mail@wired.com.
Tech
This Backyard Smoker Delivers Results Even a Pitmaster Would Approve Of

While my love of smoked meats is well-documented, my own journey into actually tending the fire started just last spring when I jumped at the opportunity to review the Traeger Woodridge Pro. When Recteq came calling with a similar offer to check out the Flagship 1600, I figured it would be a good way to stay warm all winter.
While the two smokers have a lot in common, the Recteq definitely feels like an upgrade from the Traeger I’ve been using. Not only does it have nearly twice the cooking space, but the huge pellet hopper, rounded barrel, and proper smokestack help me feel like a real pitmaster.
The trade-off is losing some of the usability features that make the Woodridge Pro a great first smoker. The setup isn’t as quite as simple, and the larger footprint and less ergonomic conditions require a little more experience or patience. With both options, excellent smoked meat is just a few button presses away, but speaking as someone with both in their backyard, I’ve been firing up the Recteq more often.
Getting Settled
Photograph: Brad Bourque
Setting up the Recteq wasn’t as time-consuming as the Woodridge, but it was more difficult to manage on my own. Some of the steps, like attaching the bull horns to the lid, or flipping the barrel onto its stand, would really benefit from a patient friend or loved one. Like most smokers, you’ll need to run a burn-in cycle at 400 degrees Fahrenheit to make sure there’s nothing left over from manufacturing or shipping. Given the amount of setup time and need to cool down the smoker after, I would recommend setting this up Friday afternoon if you want to smoke on a Saturday.
-

 Politics1 week ago
Politics1 week agoPakistan carries out precision strikes on seven militant hideouts in Afghanistan
-

 Business1 week ago
Business1 week agoEye-popping rise in one year: Betting on just gold and silver for long-term wealth creation? Think again! – The Times of India
-

 Tech1 week ago
Tech1 week agoThese Cheap Noise-Cancelling Sony Headphones Are Even Cheaper Right Now
-

 Sports1 week ago
Sports1 week agoKansas’ Darryn Peterson misses most of 2nd half with cramping
-

 Sports1 week ago
Sports1 week agoHow James Milner broke Premier League’s appearances record
-

 Entertainment1 week ago
Entertainment1 week agoSaturday Sessions: Say She She performs "Under the Sun"
-
Sports1 week ago
Mike Eruzione and the ‘Miracle on Ice’ team are looking for some company
-

 Entertainment1 week ago
Entertainment1 week agoViral monkey Punch makes IKEA toy global sensation: Here’s what it costs







