Tech
The grey door: Solving the UK’s self-inflicted skills shortage | Computer Weekly

The UK’s technology sector has had, and continues to have, a significant demographic challenge. As the nation grapples with an ageing population, the UK government has responded with fiscal policies designed to extend the working lives of its citizens, predominantly through the incremental raising of the state pension age.
Simultaneously, the IT sector, the vanguard of the modern British economy, continues to operate within a cultural and structural framework that systematically marginalises older professionals.
The premise of the current UK economic strategy is built on the assumption of “fuller working lives”. With the state pension age having risen to 66 and legislated to reach 67 between 2026 and 2028, the expectation is that workers will remain economically productive well into their late 60s.
For many sectors, this transition, while challenging, is operationally feasible. However, in the technology sector, a “grey door” appears to descend significantly earlier, often as early as age 50, creating a demographic anomaly where the industry most vital to the UK’s future is the least representative of its present population demographic.
The most definitive metric of ageism is the representation gap – the difference between the proportion of older workers in the general economy versus their proportion in the IT sector. According to the BCS diversity report 2024: “There were 446,000 IT specialists in the UK aged 50 and above during 2023, and at 22%, the level of representation for this group was much lower than that recorded amongst the wider workforce (i.e. 30%).”
The report adds: “If the level of representation for older workers in IT specialist positions was equal to that amongst the working-age population as a whole, there would have been 594,000 older IT specialists in the UK during 2023, i.e. approximately 148,000 more than the number recorded.”
This shortfall represents a significant loss of experience, leadership and technical capability, which is particularly ironic in a sector chronically complaining of skills shortages. Beyond the operational strain of the skills shortage, the structural exclusion of 148,000 experienced professionals represents a critical public policy failure, stripping the UK economy of an estimated £1.6bn in lost tax revenue and directly undermining the government’s fiscal agenda for “fuller working lives”.
According to a survey conducted by CW Jobs, “Over a third (41%) of IT and tech sector workers said they have encountered age discrimination in the workplace, whereas only 27% across other UK industries had experienced old ageism.”
The Stop the bias report 2024 from Tribepad shows similar trends.
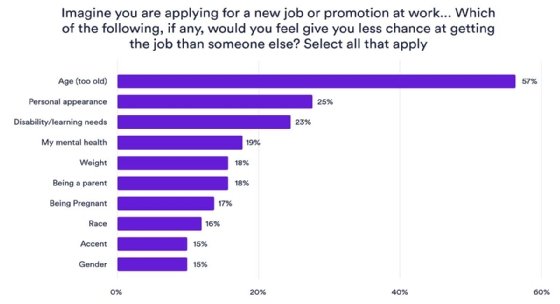
The presented trend lines offer little comfort. Despite broader societal trends towards longer careers, the level of representation for older workers in IT roles has remained stagnant over the past five years. While the general employment rate for the “50 to 64” demographic has historically trended upward, the IT sector appears resistant to this shift, maintaining a younger demographic profile as the pool of available young talent shrinks relative to the ageing population.
To resolve the conflict between an ageing demographic and a youth-centric technology sector, stakeholders must move beyond passive acknowledgement of the “grey door” to enact structural reform. When artificial intelligence (AI) tools inadvertently assert human bias, such as ageism, it threatens to turn the government’s “fuller working lives” policy into a driver of inequality.
To prevent the IT sector from becoming a closed shop to the over-50s, the following three recommendations are essential.
1. Mandate algorithmic auditing and glass box transparency
Organisations must treat AI recruitment tools as high-risk systems requiring rigorous safety checks. Companies should implement regular algorithmic audits using counterfactual testing, running identical CVs with different age markers to detect bias.
Furthermore, employers should demand transparency from software vendors regarding how their models handle proxy variables such as formatting and vocabulary, ensuring that years of experience are considered an asset rather than a liability.
2. Institutionalise and scale returnerships
While government initiatives like “returnerships” and “skills bootcamps” provide a framework, the industry must lead the execution. Tech companies should formalise corporate returner programmes as a standard recruitment channel, distinct from entry-level intakes.
These programmes should be designed to bridge the confidence and technical gaps for experienced professionals returning from career breaks, validating their transferable skills rather than forcing them to compete directly with graduates for junior roles.
3. Shift from culture fit to skills-based
The nebulous concept of “culture fit” often serves as a smokescreen for affinity bias, allowing hiring managers to reject older workers who don’t match the prevailing demographic.
Recruitment strategies must pivot to a skills-first taxonomy, where candidates are evaluated strictly on their competencies and potential contribution, rather than social similarity. This requires training human recruiters to recognise and override automation bias, ensuring they do not simply rubber-stamp the rejection of older candidates suggested by flawed AI models.
Tech
Building a Watch Collection on a Budget? Here’s Where to Start

You don’t need a four-figure Swiss movement to know what time it is—or look good doing it. One of the most wonderful things about “budget” watches today (although it’s kinder, or more appropriate, to say “affordable”) is that brands have learned to take design cues from luxury timepieces while quietly getting very good at the fundamentals: reliable movements, thoughtful materials, and proportions that don’t scream “cheap.” Take a look at the Orient in WIRED’s selection below as a prime example.
It could easily be argued that we’re in a golden age of affordable horology (see our full guide here for definitive proof), where, if you choose wisely, $350 or less can buy everything from a desirable dress watch, or a high-end collaboration, and even a supremely capable and classically chic diver. Pieces that will see you right from sunken wreck to boardroom table. And let’s not forget the retro allure of digital watches right now, either, with the Shark Classic not only being one of our favorites here, but at $70, it’s also the most affordable.
Moreover, should you decide to bag more than a few (and who could blame you at these prices?), we’ve even got the perfect carry case picked out: Nanuk’s IP67 waterproof and dustproof NK-7 resin $175 910 Watch Case (pictured above) with patented PowerClaw latching system—ideal for securing any timepiece collection, be it bargain or big budget.
Be sure to check out our other wearable coverage, including the Best Budget Watches Under $1,000, Best Smartwatches, Best Fitness Trackers, and Best Smart Rings.
Tech
I Tested 10 Popular Date-Night Boxes With My Hinge Dates

Same as the Five Senses deck above, this scratch-off card set happens in sequence, with optional “level up” cards to really push intimacy, and separate cards for each partner with secret directions. For this date, you’ll both bring a red item that you show at certain points to signify that you’re open to physical touch. Then you’ll go out to dinner and have intentional conversation, and every time a partner pulls out the red item, you’ll follow the prompts to initiate increasingly intimate physical acts, ranging from hand holding to neck kisses. So there we were, at Illegal Taqueria, edging each other over al pastor tacos (I kid).
Many of the cards urged a partner not to interrupt or solve problems, but ask questions and talk dirty. My date said, “I think this may be for couples who hate each other.” I had to agree. The second part of the date involved driving and stoplights, but since we were in Brooklyn, we walked down the trash-filled sidewalk and pretended to be a suburban couple on the fritz instead.
The rest of the date included buying things for sexy time, like whipped cream and blindfolds. I’m vegan and had no desire to lick cream from chest hair, so we came home, stripped, and did our best to keep our eyes closed (in lieu of a blindfold). It was overall a strange experience for us both, I think. If you and your partner need a lot of prompting to connect, compliment, and be physical, this set is for you.
Date: Greg, 10/10 (Note: I didn’t find this man on Hinge; I met him the old-fashioned way, in a bar at 2 am.)
Box: 6/10
Tech
WIRED’s Guide to Actually Fun Valentine’s Day Gifts

Valentine’s Day is a sneaky one. It’s easy to let grabbing fun and unique Valentine’s Day gifts fall to the wayside while you recover from the Christmas holidays, but it’s not one to miss if you have a partner you want to shower with a little extra love.
If you’re feeling too wiped to shop, good news: I’ve got you covered. I’ve rounded up some of our favorite ideas for the year’s most romantic holiday, from Lego sets you can build as a date and date boxes filled with ideas to last you all year long to gorgeous flowers you can get delivered in a snap and cozy robes you’ll want to lounge in together. This guide all the Valentine’s Day gifts we’re excited to give this year.
Curious about what else we recommend? Don’t miss our Gifts for Lovers, Gifts for Moms, Gifts for Plant Lovers, Gifts for People Who Work from Home, and Best Blind Boxes for more gifts and shopping ideas.
Table of Contents
For a Gift That’s a Date
My husband and I are planning our fourth or fifth year of our favorite Valentine’s Day Date: building Lego sets together. We’ve done this for years, and then we get to enjoy the fruits (well, flowers) of our labor around the home forevermore. These sets serve as both the gift and the activity. Building the dried-flower centerpiece together was probably my all-time favorite, since you can each simultaneously work on one half and then click it together at the end, followed by each building a different-color bonsai tree.
For a Daytime Adventure
Building on the idea of date activities that involve gifts, this multi-person paddleboard is a fun way to spend time outdoors while staying together the entire time. It’s massive, almost raftlike, so that it can support the weight of up to three adults, but once we got the hang of the size, it wasn’t hard to maneuver. Sometimes we’d both row together, sometimes I’d let my husband do all the work. It made for a lovely daytime adventure together, and I can’t wait for the next warm day for my husband and me to take this out on our local harbor again. It’s big enough that we could bring our son, though it’s much more peaceful as a date activity. It’s inflatable, and I’d recommend grabbing an electric filler since it takes a lot of manual pumping otherwise.
For Flowers on Demand
The classic go-to for Valentine’s Day is, of course, flowers. WIRED reviewer Boutayna Chokrane tested several flower delivery services to find the best one to get sent to your home, and her favorite is the Ode à la Rose, specifically the Edith arrangements. The business was created by two former French bankers, and the arrangements’ design choices feel distinctly chic in a way only French romance can. The Edith bouquet is entirely Columbus double tulips from Holland, and come hand-tied in a travel vase a fun pink box. The flowers ship nationwide, and there’s same-day shipping in New York, Chicago, Los Angeles, Austin, Miami, and Washington, DC.
For a Jewelry Upgrade
Maybe you’ve already exchanged rings, or maybe you’re looking for your first set without committing to I do. Either way, the most popular fitness tracker to get these days is a smart ring, and Oura is the ruler of the space. The latest model is the Ring 4, and it comes in both metallic and ceramic finishes. Many of my friends love theirs. I wish I had one, but they don’t make sense for my husband and me since we’re an aerialist and rock climber duo. Live my dreams for me and get this for your valentine (and yourself)!
For Your Fave Photographer
If your romantic partner loves to capture photos, a digital photo frame is the perfect gift (and you’ll benefit, too, as likely the number one fan of their photography!). I’m the photographer of our house, and our Aura frame is my husband’s favorite gadget because it showcases photos I’ve captured of our son and life together over the years. Our wedding photos can be found on there too, as well as the occasional good photo of me that he’s captured. It’s a monthly ritual for me to go through my camera roll and add my latest favorites. Aura’s my favorite because the range of frames is beautiful, and the storage is unlimited with no fees or subscriptions.
For the Cozy Couple
One of my favorite souvenirs I have around the house is a matching robe set that my husband and I bought on our honeymoon. Our all-cotton robes are from the Ten Thousand Waves Japanese spa in New Mexico (the final destination of a Southwestern US road trip) and are great for taking to the pool or using after a shower on a hot day. But I still love a good fluffy robe during the colder season, especially since it can double as a towel. Get your partner one of these cozy robes to give them something luxurious to use after their next everything shower or quick rinse-off. Cozy Earth’s robe is crazy-soft thanks to its blend of cotton and bamboo viscose, while this flannel robe from L.L.Bean is one of our favorites for anyone who works from home.
For Your Inner Theater Kids
If your partner loves to sing along to the Wicked soundtrack and is regularly suggesting karaoke as a group activity, then give them the gift of making karaoke happen anywhere with these gadgets. The Bonaok Karaoke Microphone is one of our favorite karaoke microphones, letting you sing anywhere without lugging bulky equipment. The Ikarao Shell S2 is a portable device with two mics, a built-in screen, and support for streaming services, so you can sing along to your favorite songs on Spotify.
For the Fitness Couple
After the Christmas season, I saw a video on my For You page that roasted how every mom had clearly gotten a matching workout outfit set for Christmas and was out wearing it on Boxing Day. As a mom myself, all I could think of was how much I would love another matching workout set. I’m serious. They’re great for workouts, quick errands, and day care or school drop-off. My latest favorite set is from Bombshell Sportswear. The set is both super soft and fits securely without any annoying squeezing. It’s getting the most compliments of all my sets. I wish I’d sized up with the bolero, but as an aerialist, my lat muscles are a little bulkier than an everyday person’s.
Have a partner who doesn’t need a matching set? Try some fantastic running shoes instead, which are even more useful for both workouts and daily life. WIRED reviewer Adrienne So says these R.A.D. shoes are fantastic for a range of uses, as they’re designed for gym, HIIT, CrossFit, and hybrid workouts and are soft enough for treadmill running. They look fantastic, too.
For the Beloved Bookworms
A Kindle is always a great gift for anyone who reads in any format. Funny enough, my siblings and I are about to buy one for my dad for his birthday (two weeks before Valentine’s Day), and I recommended my favorite pick, the Kindle Paperwhite, since the standard Kindle is a little too small for his 6-foot-4 frame to hunch down over, and he doesn’t read enough illustrated books to make the Colorsoft the right jump for him. If they already have a Kindle, I’m still in love with my matching PopSockets Kindle case and grip, and they’ve since launched a new Bookish collection with beautiful designs.
For Some Bedroom Spice
Looking to spice things up? These adventure boxes can add more fun to the bedroom without creating additional mental work for you and your partner. An offshoot from the Adventure Challenge, “The Adventure Challenge … In Bed” scratch-off date book has 50 date ideas designed specifically to help facilitate fun and connection in the bedroom. The dates are categorized by activity type in sections like food, dancing, “sexploration,” and more. Each date is covered by a black box, with only icons indicating required fields such as duration, cost, and more. Meanwhile, the Fantasy Box is a date-night box service offering a range of themes, from sexy wine tasting to a kinky poker night, all designed to help couples communicate and connect more intimately. Before opening the box, each partner will fill out a questionnaire of potential intimate acts, and this box comes with everything needed for a truly kinky night in: a satin blindfold, pleather paddle, lingerie, lube, massage gel, feather wand, mini vibrator, and silky wrist restraints. —Molly Higgins
Power up with unlimited access to WIRED. Get best-in-class reporting and exclusive subscriber content that’s too important to ignore. Subscribe Today.
-

 Sports6 days ago
Sports6 days agoPSL 11: Local players’ category renewals unveiled ahead of auction
-

 Entertainment5 days ago
Entertainment5 days agoClaire Danes reveals how she reacted to pregnancy at 44
-

 Tech1 week ago
Tech1 week agoICE Asks Companies About ‘Ad Tech and Big Data’ Tools It Could Use in Investigations
-

 Business6 days ago
Business6 days agoBanking services disrupted as bank employees go on nationwide strike demanding five-day work week
-

 Fashion1 week ago
Fashion1 week agoSpain’s apparel imports up 7.10% in Jan-Oct as sourcing realigns
-

 Sports6 days ago
Sports6 days agoCollege football’s top 100 games of the 2025 season
-

 Politics1 week ago
Politics1 week agoFresh protests after man shot dead in Minneapolis operation
-

 Business1 week ago
Business1 week agoShould smartphones be locked away at gigs and in schools?









