Tech
ICO publishes summary of police facial recognition audit | Computer Weekly

The Information Commissioner’s Office (ICO) has completed its first-ever data protection audit of UK police forces deploying facial recognition technologies (FRT), noting it is “encouraged” by its findings.
The ICO’s audit, which investigated how South Wales Police and Gwent Police are using and protecting people’s personal information when deploying facial recognition, marks the first time the data regulator has formally audited a UK police force for its use of the technology.
According to an executive summary published on 20 August, the scope of the facial recognition audit – which was agreed with the two police forces beforehand – focused on questions of necessity and proportionality (a key legal test for the deployment of new technologies), whether its design meets expectations around fairness and accuracy, and whether “the end-to-end process” is compliant with the UK’s data protection rules.
“We are encouraged by the findings, which provide a high level of assurance that the processes and procedures currently in place at South Wales Police and Gwent Police are compliant with data protection law,” said the deputy commissioner for regulatory policy, Emily Keaney, in a blog post.
“The forces made sure there was human oversight from trained staff to mitigate the risk of discrimination and ensure no decisions are solely automated, and a formal application process to assess the necessity and proportionality before each LFR deployment,” she wrote.
The executive summary added that South Wales Police and Gwent Police have “comprehensively mapped” their data flows, can “demonstrate the lawful provenance” of the images used to generate biometric templates, and have appropriate data protection impact assessments (DPIAs) in place.
It further added that the data collected “is adequate, relevant and limited to what is necessary for its purpose”, and that individuals are informed about its use “in a clear and accessible manner”.
However, Keaney was clear that the audit only “serves as a snapshot in time” of how the technology is being used by the two police forces in question. “It does not give the green light to all police forces, but those wishing to deploy FRT can learn from the areas of assurance and areas for improvement revealed by the audit summary,” she said.
Commenting on the audit, chief superintendent Tim Morgan of the joint South Wales and Gwent digital services department, said: “The level of oversight and independent scrutiny of facial recognition technology means that we are now in a stronger position than ever before to be able to demonstrate to the communities of South Wales and Gwent that our use of the technology is fair, legitimate, ethical and proportionate.
“We welcome the work of the Information Commissioner’s Office audit, which provides us with independent assurance of the extent to which both forces are complying with data protection legislation.”
He added: “It is important to remember that use of this has never resulted in a wrongful arrest in South Wales and there have been no false alerts for several years as the technology and our understanding has evolved.”
Lack of detail
While the ICO provided a number of recommendations to the police forces, it did not provide any specifics in the executive summary beyond the priority level of the recommendation and whether it applied to the forces’ use of live or retrospective facial recognition (LFR or RFR).
For LFR, it said it made four “medium” and one “low” priority recommendations, while for RFR, it said it made six “medium” and four “low” priority recommendations. For each, it listed one “high” priority recommendation.
Computer Weekly contacted the ICO for more information about the recommendations, but received no response on this point.
Although the summary lists some “key areas for improvement” around data retention policies and the need to periodically review various internal procedures, key questions about the deployments are left unanswered by the ICO’s published material on the audit.
For example, before they can deploy any facial recognition technology, UK police forces must ensure their deployments are “authorised by law”, that the consequent interference with rights – such as the right to privacy – is undertaken for a legally “recognised” or “legitimate” aim, and that this interference is both necessary and proportionate. This must be assessed for each individual deployment of the tech.
However, beyond noting that processes are in place, no detail was provided by the ICO on how the police forces are assessing the necessity and proportionality of their deployments, or how these are assessed in the context of watchlist creation.
Although more detail on proportionality and necessity considerations is provided in South Wales Police’s LFR DPIA, it is unclear if any of the ICO’s recommendations concern this process.
While police forces using facial recognition have long maintained that their deployments are intelligence-led and focus exclusively on locating individuals wanted for serious crimes, senior officers from the Metropolitan Police and South Wales Police previously admitted to a Lords committee in December 2023 that both forces select images for their watchlists based on crime categories attached to people’s photos, rather than a context-specific assessment of the threat presented by a given individual.
Computer Weekly asked the ICO whether it is able to confirm if this is still the process for selecting watchlist images at South Wales Police, as well as details on how well police are assessing the proportionality and necessity of their deployments generally, but received no response on these points.
While the ICO summary claims the forces are able to demonstrate the “lawful provenance” of watchlist images, the regulator similarly did not respond to Computer Weekly’s questions about what processes are in place to ensure that the millions of unlawfully held custody images in the Police National Database (PND) are not included in facial recognition watchlists.
Computer Weekly also asked why the ICO is only beginning to audit police facial recognition use now, given that it was first deployed by the Met in August 2016 and has been controversial since its inception.
“The ICO has played an active role in the regulation of FRT since its first use by the Met and South Wales Police around 10 years ago. We investigated the use of FRT by the Met and South Wales and Gwent police and produced an accompanying opinion in 2021. We intervened in the Bridges case on the side of the claimant. We have produced follow-up guidance on our expectations of police forces,” said an ICO spokesperson.
“We are stepping up our supervision of AI [artificial intelligence] and biometric technologies – our new strategy includes a specific focus on the use of FRT by police forces. We are conducting an FRT in Policing project under our AI and biometrics strategy. Audits form a core part of this project, which aims to create clear regulatory expectations and scalable good practice that will influence the wider AI and biometrics landscape.
“Our recommendations in a given audit are context-specific, but any findings that have applicability to other police forces will be included in our Outcomes Report due in spring 2026, once we have completed the rest of the audits in this series.”
EHRC joins judicial review
In mid-August 2025, the Equality and Human Rights Commission (EHRC) was granted permission to intervene in an upcoming judicial review of the Met Police’s use of LFR technology, which it claims is being deployed unlawfully.
“The law is clear: everyone has the right to privacy, to freedom of expression and to freedom of assembly. These rights are vital for any democratic society,” said EHRC chief executive John Kirkpatrick.
“As such, there must be clear rules which guarantee that live facial recognition technology is used only where necessary, proportionate and constrained by appropriate safeguards. We believe that the Metropolitan Police’s current policy falls short of this standard.”
He added: “The Met, and other forces using this technology, need to ensure they deploy it in ways which are consistent with the law and with human rights.”
Writing in a blog about the EHRC joining the judicial review, Chris Pounder, director of data protection training firm Amberhawk, said that, in his view, the statement from Kirkpatrick is “precisely the kind of statement that should have been made by” information commissioner John Edwards.
“In addition, the ICO has stressed the need for FRT deployment ‘with appropriate safeguards in place’. If he [Edwards] joined the judicial review process as an interested party, he could get judicial approval for these much vaunted safeguards (which nobody has seen),” he wrote.
“Instead, the ICO sits on the fence whilst others determine whether or not current FRT processing by the Met Police is ‘strictly necessary’ for its law enforcement functions. The home secretary, for her part, has promised a code of practice which will contain an inevitable bias in favour of the deployment of FRT.”
In an appearance before the Lords Justice and Home Affairs Committee on 8 July, home secretary Yvette Cooper confirmed the government is actively working with police forces and unspecified “stakeholders” to draw up a new governance framework for police facial recognition.
However, she did not comment on whether any new framework would be placed on a statutory footing.
Tech
Wake Up—the Best Cyber Monday Mattress and Bedding Sales Are Here

If you’ve been dreaming all year of saving serious cash on a new mattress, you have a few more hours before the alarm goes off. From the best mattresses for back pain to our favorite cooling options, these are the top deals on mattresses the WIRED Reviews team has tested in their own homes. We also track prices all year to see where the best sales are really happening. And Cyber Monday brings some of the best sleep deals you’ll see all year.
If it’s on this list, it’s genuinely a good deal on a product someone from our team has tested and approved of. While the prices listed below are for queen sizes, the deals should apply to all mattress sizes. Your dreams of a new king mattress are still going strong.
Updated 2 pm ET December 1: We’ve added new sales from Sleep Number and Thuma, and ensured up-to-date links and prices.
WIRED Featured Deals
Bear
The WIRED Reviews team has crowned the Bear Elite Hybrid as the best mattress for back pain we’ve tested to date. It comes in three firmness options, including Soft, Medium, and Firm. WIRED testers have found Firm helpful for spinal alignment, and you can also add a Celliant cover for a fee, designed to help with muscle recovery. In addition to the sale, Bear is also throwing in a free accessories bundle (two pillows, a sheet set, and a mattress protector). Use WIRED40 for 40 percent off, which is an additional 5 percent off the offer you’ll see on the site.
Helix
We test many, many mattresses—so it’s saying something that the Helix Midnight Luxe has been our favorite overall mattress for seven years running. This specific model is designed for side sleepers, but the brand’s slogan is “designed for every body,” and there are plenty of options for every sleeping position. Helix’s Cyber Week sale is underway, but you can get additional savings by using our exclusive coupon code WIRED27 for 27 percent off.
Saatva
Saatva mattresses strive to be the intersection of luxury, natural materials, and support for many sleepers. One model in particular that we’ve tested, the Saatva Rx, offers serious pressure relief for even the most persistent aches and pains. It incorporates micro coils and pressure-relief foam, so the price is usually on the higher side. However, Saatva’s holiday sales promo should take some strain off your wallet, as you can save $400 off purchases of $1,000 or more. Use our link below.
Sleep Number
If you’re trying to decide between a sleep tracker or a new mattress, I’ve got news for you—Sleep Number can do both. The p6 is a smart bed that lets you adjust your preferred firmness; pressure relief levels; and, paired with an adjustable base, the angle of the head and foot of the bed. It also tracks your sleep, noting any changes in your heart rate, breathing, and deep sleep. Sleep Number is offering free shipping plus discounts for bed and base bundles. Free shipping’s a big deal because it’s usually a separate fee from Sleep Number for a team to come set up the bed for you. Now, it’s just part of your purchase.
Casper
Amazon’s current price on this Casper hybrid is slightly lower than we saw for Prime Day, at just over $1,000 for a queen from Amazon. Casper was one of the original American mattresses-in-a-box makers, though the company has been bought and sold a few times. We like this mattress for pressure relief but it has heightened support thanks to the coils. There’s also a sale on a Casper pillow we like below.
Birch
If you’re looking to get memory foams and other man-made materials out of your bedroom in favor of an all-organic mattress, the Birch Luxe Natural has been a consistent winner for us. It has an organic cotton Euro top that gives your pressure points a cushioned surface to slightly sink into. Layers of natural wool are incorporated underneath for breathable temperature control. Latex is pressure-relieving, like memory foam, but without any chemicals involved. It’s also organic, with Global Organic Latex Standard (GOLS) certification. Pocketed coils help support you where you need it most. Birch is also throwing in two free pillows with every mattress purchase. To make it even better, you can use code WIRED27 for even more savings.
Airweave
There is a significant savings on a mattress we really liked for its firmness and portability, while balking at the price in our review. The Airweave’s filling is made from a unique ultrafine woven polyethylene, which looks like uncooked glass noodles or a tangle of fishing line. It functions like super micro coils and offers a somewhat stiff but very. supportive sleeping surface. Best of all, it can be disassembled for easy moving, and the cover is washable.
Silk & Snow
Canadian brand Silk & Snow uses high-quality materials and thoughtful construction in its mattresses, with prices that are hard to argue with. In the S&S Organic hybrid’s case, there are several organic certifications too. With GOLS-certified organic cotton, organic wool, and GOLS-certified latex atop pocketed coils, it eliminates any guesswork about materials and focuses solely on support. For holiday shoppers, Silk & Snow is offering up to $300 off on mattresses, no code needed.
Avocado
Avocado takes the notion of “all-natural” mattresses very seriously, with an extensive list of certifications to back its claims. The Avocado Green hybrid mattress comes in Firm (base model), Medium (pillow top), and Plush (box top, which is an even thicker version of a softer pillow top). Medium and Plush cost a bit extra, but we previously tested the Firm model and loved it. Its organic latex and coil construction provided lumbar support, temperature regulation, and pressure relief to the point where it got a near-perfect score. For Avocado’s holiday mattress sale, you can take 20 percent off your purchase, no code needed.
Wolf
Wolf mattresses are not ones you should overlook. Each time our team has tested a Wolf mattress, we were impressed with its quality and performance. The Wolf 13-Inch Memory Foam Hybrid Premium Firm Mattress is quite a name, but this hybrid mattress excels with temperature control thanks to a cooling cover, foams, and coils. It’s just firm enough that you can move around without feeling stuck, and it also maintains spinal alignment. Wolf’s Cyber Week mattress sale is now live, with 15 percent off on your purchase.
Tiami
Tiami’s Luxury Hybrid has a firmer feel with cushioning memory foam layers and unique, foam-capped coils that help relieve pressure around your joints. It’s a specialty mattress through and through, which makes Tiami’s current mattress sale even more enticing. It’s the lowest price we’ve seen all year, thanks to its Cyber Monday promo at 40 percent off, no code needed.
Essentia
You’re searching high and low for an organic mattress, but not just any organic mattress will do—it has to be vegan as well. (Many organic mattresses aren’t vegan due to the inclusion of wool.) For those who aim to live (and sleep!) by vegan protocols, Essentia’s Tatami mattress is right up your alley. It’s got organic cotton, organic latex, and organic foam all meant for pressure relief, temperature control, and strong lumbar support. Essentia is offering 25 percent off mattresses plus two free pillows as part of its holiday mattress sale. (Discount reflected in cart.)
Naturepedic
Naturepedic checks a lot of boxes with its EOS Classic mattress. It’s got customizable firmness on each side of the mattress. It’s one of the best mattresses we’ve tested to date. It’s also made with organic materials, making it one of the best organic mattresses we’ve come across. Naturepedic is offering 20 percent off sitewide and throwing in a free accessories bundle (organic mattress protector and pillows) on orders of $699 or more.
Leesa
Leesa’s Sapira Chill Hybrid ranks as one of the best mattresses by our account (more specifically, the best hybrid mattress), thanks to its cooling and lumbar support. It features a quilted pillow top with a cooling cover, along with pressure-relieving foams and pocketed coils. There are three firmness levels to choose from, but if you have back pain, you may want to opt for something firmer to support spine alignment. Plus, the Sapira Chill’s pillow top will soften things out a bit. While the price for this mattress isn’t the lowest we’ve seen this year, Leesa’s holiday sale is pretty good. You can take 30 percent off select mattresses, including the Sapira Chill.
Plank
For those who feel like a mattress is never quite firm enough, the Plank Firm is one of the team’s favorite beds that delivers a truly firm feel. It’s actually dual-sided, with one side “firm” and the other “extra firm,” so you can get the utmost, unyielding support. It’s been a hit with some of our testers who have back pain and look to firm beds to maintain spine alignment. To keep your wallet balanced, too, Plank is offering 30 percent off with code BFRIDAY30.
Cyber Monday Bedding Deals
No new mattress setup would be complete without sheets, pillows, bed frames, and sleep accessories. Cyber Monday is the time to get the best of the best, and these are deals we’re pretty hyped about.
Thuma Signature Bed Frame
We’re big Thuma fans around here, from the Thuma Hybrid mattress to its Classic Bed frame (review coming soon!). We wish these two items were on sale for Black Friday, but Cyber Monday is a new day with new opportunities, like a sale on Thuma’s Signature Bed frame. Just like the Classic Bed, the Signature Bed frame is a cinch to set up and comes in either soft Italian felt or performance linen. Thuma is offering up to 22 percent off the Signature Bed as part of its Cyber Monday sale.
Casper Sleep Hybrid Snow Pillow
Another Casper sale you’ll find on Amazon, reviewer Nena Farrell found this pillow had a lower loft paired with a firmer feel. These are both aspects that stomach sleepers need from their pillows to prevent disturbing their neck’s cervical alignment and causing trouble with their lower backs.
My Green Mattress
You’re looking for a quick hack to revitalize your mattress’s support—before your guests arrive for the holidays. Mattress toppers can help buy you some time while increasing pressure relief, support, and overall comfort. This organic latex mattress topper from My Green Mattress has two inches of firmer-feeling, GOLS-certified Dunlop latex. For the holiday, you can get 15 percent off sleep accessories, including this organic latex topper.
Helix
Here’s another hypothetical for you, based on personal experience: You know someone living in a dorm, and their mattress just straight-up sucks. Sleep’s crucial for these scholars, and Helix’s GlacioTex Memory Foam Topper is designed to provide pressure relief and temperature regulation to help elevate the lowliest of dorm-room beds (aka, a glorified piece of foam wrapped in a tarp). Use code WIRED27 for 27 percent off this topper.
Cozy Earth
We’re covering all sorts of Cozy Earth deals right now. But these bamboo sheets are so lovely, we’re giving them a shoutout twice. If you’re still struggling with gift ideas, these sheets are a cooling, luxurious option the recipient will use often (at least, I’d sure use them). Plus, the limited edition seasonal patterns are too whimsical to pass up. These sheets are currently 45 percent off and are selling out quickly.
Brooklinen
If you crave the experience of being wrapped in something similar to a fluffy cloud, chances are you’d really like a down comforter. WIRED reviewer Louryn Strampe likened Brooklinen’s all-season down comforter to something you’d see in a hotel, with its starchy cover and fluffy fill. Brooklinen is continuing its 25 percent off sitewide sale from Black Friday through Cyber Week.
Coop
The first time I technically tested this crescent pillow was in a friend’s guest room, and I’ve been a fan ever since. This adjustable pillow’s bottom has an arch, allowing your shoulders to press into the pillow and providing more cushion around your neck. You can also add fill (which comes in a separate bag) to make it firmer, or take some out to increase softness. You can take 25 percent off as part of its current sitewide sale.
Power up with unlimited access to WIRED. Get best-in-class reporting and exclusive subscriber content that’s too important to ignore. Subscribe Today.
Tech
I’ve Tried Every Digital Notebook. Here Are the Best Ones on Sale

I love a digital notebook. I write about them all year long here at WIRED, and it’s not often my favorites go on sale. (Or for any to go on sale, besides Amazon’s own sale events.) But this year, multiple digital notebooks I love are on sale for the biggest sale event of the year.
If you’ve thought about getting one of these for yourself, there’s truly no better moment. From reMarkable’s on-sale bundles to Kobo’s deals, you can shop five of the best digital notebooks we’ve ever tried right now at a lower price than you might find until next year. They’re a handy device just about everyone can enjoy, whether you want to digitally annotate your books or write out your grocery list without using a piece of paper.
Looking for more great sales to shop? Don’t miss our guides to the Best Amazon Device and Kindle Deals, Best Laptop Deals, the Absolute Best Cyber Monday Deals, and our liveblog.
Update Dec. 1: We updated prices, links, and deals, and added the Rocketbook Fusion Plus notebook.
The Best Digital Notebook Deals
Some of the best digital notebooks we’ve tried come from reMarkable, and one of reMarkable’s models always seems to reign supreme over our digital notebooks guide. While the Paper Pro Move is the newest model, the reMarkable Paper Pro that launched in September 2024 is my current all-around favorite. It’s not only powerful with tons of tools and an easy interface, but packs a color screen for colorful notes. It also has a gentle front light so that you can use it in darker environments. You can get the bundles on sale right now, so combine one of reMarkable’s markers and folio covers with a Paper Pro to get $50 off.
The best discount from reMarkable is actually for its older device and our previous top pick, the reMarkable 2. It doesn’t have a color screen or the front light, but you’ll get the reMarkable’s great software and options for accessories like the Keyboard Folio to use it like a laptop. The reMarkable 2 bundles are also on sale, so add on your favorite folio of choice on reMarkable’s website to get $70 off.
The Kobo Libra Colour is my favorite all-around e-reader with its color screen and page turner buttons, but you can add on a stylus to have it double as a digital notebook. It’s one of the more affordable options, and it’s a smaller screen than the rest of these, but I especially love that you can use the stylus to doodle on the books you’re reading (something you can’t do with the Kindle Scribe). It’s $30 off on Kobo’s site for Cyber Monday.
The second-generation Kindle Scribe isn’t the best digital notebook, but the long battery life (12 weeks!!) and convenient starting point of it being a Kindle I could already be reading on makes it a great go-to for casual notetakers and doodlers. It’s a good choice for Kindle and Amazon users, and there are new models due out this winter, but they likely won’t be as cheap as this one. (Especially since some of those new models will have color!)
If you like the idea of getting a Kobo e-reader that doubles as a digital notebook, you can go for more of a classic size with the larger Elipsa 2E. This one comes with the stylus, so you won’t have to add it on, and it’s $50 off.
The Rocketbook Fusion Plus digital planner and notebook is for those who don’t want to charge their notebook or give up on the whole “paper” experience. Take notes with the included, erasable Pilot Frixion Pen, scan photos of the pages into the app, and erase the whole thing with the damp microfiber cloth (also included). Fusion Plus is on its steepest discount of recent memory, and comes templates that range from monthly and weekly pages to project management and meeting notes.
Power up with unlimited access to WIRED. Get best-in-class reporting and exclusive subscriber content that’s too important to ignore. Subscribe Today.
Tech
Artificial tendons give muscle-powered robots a boost
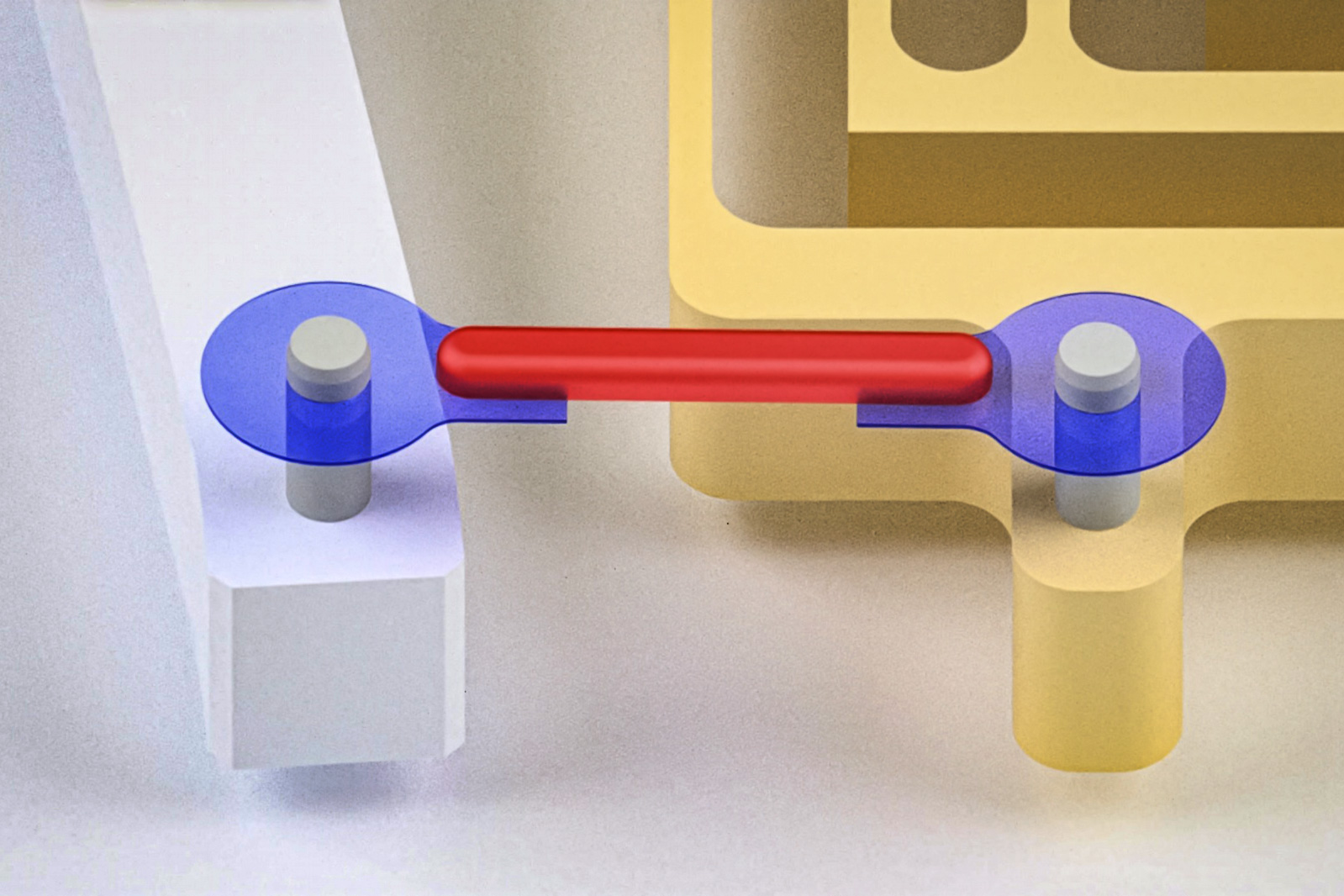
Our muscles are nature’s actuators. The sinewy tissue is what generates the forces that make our bodies move. In recent years, engineers have used real muscle tissue to actuate “biohybrid robots” made from both living tissue and synthetic parts. By pairing lab-grown muscles with synthetic skeletons, researchers are engineering a menagerie of muscle-powered crawlers, walkers, swimmers, and grippers.
But for the most part, these designs are limited in the amount of motion and power they can produce. Now, MIT engineers are aiming to give bio-bots a power lift with artificial tendons.
In a study appearing today in the journal Advanced Science, the researchers developed artificial tendons made from tough and flexible hydrogel. They attached the rubber band-like tendons to either end of a small piece of lab-grown muscle, forming a “muscle-tendon unit.” Then they connected the ends of each artificial tendon to the fingers of a robotic gripper.
When they stimulated the central muscle to contract, the tendons pulled the gripper’s fingers together. The robot pinched its fingers together three times faster, and with 30 times greater force, compared with the same design without the connecting tendons.
The researchers envision the new muscle-tendon unit can be fit to a wide range of biohybrid robot designs, much like a universal engineering element.
“We are introducing artificial tendons as interchangeable connectors between muscle actuators and robotic skeletons,” says lead author Ritu Raman, an assistant professor of mechanical engineering (MechE) at MIT. “Such modularity could make it easier to design a wide range of robotic applications, from microscale surgical tools to adaptive, autonomous exploratory machines.”
The study’s MIT co-authors include graduate students Nicolas Castro, Maheera Bawa, Bastien Aymon, Sonika Kohli, and Angel Bu; undergraduate Annika Marschner; postdoc Ronald Heisser; alumni Sarah J. Wu ’19, SM ’21, PhD ’24 and Laura Rosado ’22, SM ’25; and MechE professors Martin Culpepper and Xuanhe Zhao.
Muscle’s gains
Raman and her colleagues at MIT are at the forefront of biohybrid robotics, a relatively new field that has emerged in the last decade. They focus on combining synthetic, structural robotic parts with living muscle tissue as natural actuators.
“Most actuators that engineers typically work with are really hard to make small,” Raman says. “Past a certain size, the basic physics doesn’t work. The nice thing about muscle is, each cell is an independent actuator that generates force and produces motion. So you could, in principle, make robots that are really small.”
Muscle actuators also come with other advantages, which Raman’s team has already demonstrated: The tissue can grow stronger as it works out, and can naturally heal when injured. For these reasons, Raman and others envision that muscly droids could one day be sent out to explore environments that are too remote or dangerous for humans. Such muscle-bound bots could build up their strength for unforeseen traverses or heal themselves when help is unavailable. Biohybrid bots could also serve as small, surgical assistants that perform delicate, microscale procedures inside the body.
All these future scenarios are motivating Raman and others to find ways to pair living muscles with synthetic skeletons. Designs to date have involved growing a band of muscle and attaching either end to a synthetic skeleton, similar to looping a rubber band around two posts. When the muscle is stimulated to contract, it can pull the parts of a skeleton together to generate a desired motion.
But Raman says this method produces a lot of wasted muscle that is used to attach the tissue to the skeleton rather than to make it move. And that connection isn’t always secure. Muscle is quite soft compared with skeletal structures, and the difference can cause muscle to tear or detach. What’s more, it is often only the contractions in the central part of the muscle that end up doing any work — an amount that’s relatively small and generates little force.
“We thought, how do we stop wasting muscle material, make it more modular so it can attach to anything, and make it work more efficiently?” Raman says. “The solution the body has come up with is to have tendons that are halfway in stiffness between muscle and bone, that allow you to bridge this mechanical mismatch between soft muscle and rigid skeleton. They’re like thin cables that wrap around joints efficiently.”
“Smartly connected”
In their new work, Raman and her colleagues designed artificial tendons to connect natural muscle tissue with a synthetic gripper skeleton. Their material of choice was hydrogel — a squishy yet sturdy polymer-based gel. Raman obtained hydrogel samples from her colleague and co-author Xuanhe Zhao, who has pioneered the development of hydrogels at MIT. Zhao’s group has derived recipes for hydrogels of varying toughness and stretch that can stick to many surfaces, including synthetic and biological materials.
To figure out how tough and stretchy artificial tendons should be in order to work in their gripper design, Raman’s team first modeled the design as a simple system of three types of springs, each representing the central muscle, the two connecting tendons, and the gripper skeleton. They assigned a certain stiffness to the muscle and skeleton, which were previously known, and used this to calculate the stiffness of the connecting tendons that would be required in order to move the gripper by a desired amount.
From this modeling, the team derived a recipe for hydrogel of a certain stiffness. Once the gel was made, the researchers carefully etched the gel into thin cables to form artificial tendons. They attached two tendons to either end of a small sample of muscle tissue, which they grew using lab-standard techniques. They then wrapped each tendon around a small post at the end of each finger of the robotic gripper — a skeleton design that was developed by MechE professor Martin Culpepper, an expert in designing and building precision machines.
When the team stimulated the muscle to contract, the tendons in turn pulled on the gripper to pinch its fingers together. Over multiple experiments, the researchers found that the muscle-tendon gripper worked three times faster and produced 30 times more force compared to when the gripper is actuated just with a band of muscle tissue (and without any artificial tendons). The new tendon-based design also was able to keep up this performance over 7,000 cycles, or muscle contractions.
Overall, Raman saw that the addition of artificial tendons increased the robot’s power-to-weight ratio by 11 times, meaning that the system required far less muscle to do just as much work.
“You just need a small piece of actuator that’s smartly connected to the skeleton,” Raman says. “Normally, if a muscle is really soft and attached to something with high resistance, it will just tear itself before moving anything. But if you attach it to something like a tendon that can resist tearing, it can really transmit its force through the tendon, and it can move a skeleton that it wouldn’t have been able to move otherwise.”
The team’s new muscle-tendon design successfully merges biology with robotics, says biomedical engineer Simone Schürle-Finke, associate professor of health sciences and technology at ETH Zürich.
“The tough-hydrogel tendons create a more physiological muscle–tendon–bone architecture, which greatly improves force transmission, durability, and modularity,” says Schürle-Finke, who was not involved with the study. “This moves the field toward biohybrid systems that can operate repeatably and eventually function outside the lab.”
With the new artificial tendons in place, Raman’s group is moving forward to develop other elements, such as skin-like protective casings, to enable muscle-powered robots in practical, real-world settings.
This research was supported, in part, by the U.S. Department of Defense Army Research Office, the MIT Research Support Committee, and the National Science Foundation.
-

 Sports1 week ago
Sports1 week agoWATCH: Ronaldo scores spectacular bicycle kick
-

 Entertainment1 week ago
Entertainment1 week agoWelcome to Derry’ episode 5 delivers shocking twist
-

 Politics1 week ago
Politics1 week agoWashington and Kyiv Stress Any Peace Deal Must Fully Respect Ukraine’s Sovereignty
-

 Business1 week ago
Business1 week agoKey economic data and trends that will shape Rachel Reeves’ Budget
-

 Tech6 days ago
Tech6 days agoWake Up—the Best Black Friday Mattress Sales Are Here
-

 Politics1 week ago
Politics1 week ago53,000 Sikhs vote in Ottawa Khalistan Referendum amid Carney-Modi trade talks scrutiny
-

 Fashion1 week ago
Fashion1 week agoCanada’s Lululemon unveils team Canada kit for Milano Cortina 2026
-

 Tech1 day ago
Tech1 day agoGet Your Steps In From Your Home Office With This Walking Pad—On Sale This Week


.jpg)
-Partner-Photo-SOURCE-Wired-(edited-R0000095).jpg)
-SOURCE-Nena-Farrell.jpg.jpg)




.jpg)


-Reviewer-Photo-SOURCE-Scott-Gilbertson.jpg)
-Reviewer-Photo-SOURCE-Scott-Gilbertson.jpg)
-82.jpg)









.jpg)

.jpg)
.jpg)



.jpg)



-Reviewer-Photo-SOURCE-Louryn-Strampe.jpg)


-Reviewer-Photo-SOURCE-Nena-Farrell.jpg)










