


If your team is still in the running, you may be in the market for a new TV to watch the big game, and TCL has...



The British and Chinese authorities have reached out to one another to explore setting up a cyber security forum between the two countries, according to...



Days after Micron broke ground on a $100 billion chip factory in New York state, a coalition of environmentalists, labor unions, and civil rights groups are...

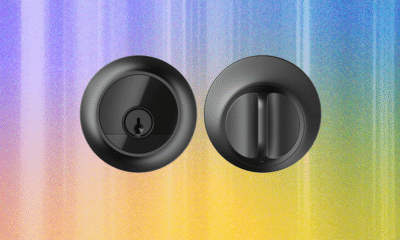

But this lock’s interior deadbolt manages to hold an impressive amount of technology. There’s a new dual-core chipset that has a ton of compatibility and unlocking...



Barry Panayi, group chief data officer (CDO) at insurance firm Howden, is on a mission to create what he calls the datasphere. Rather than simply...



The latest filings in Tesco’s £100m lawsuit against Broadcom and VMware over an alleged breach in software licensing terms demonstrates the complexity in dealing with...



Want to be the hero of your next Super Bowl party? Check out the Ninja Crispi Portable Glass Air Fryer, an intriguing twist on the air...



All-Clad Deals used to be difficult to find, but thankfully, the Factory Seconds Sale has come back around for a little while. These sales tend to...



Justice for Far Side cartoonist Gary Larson: A team of scientists has observed, for the first time, a cow using a tool in a flexible manner....



Unverified and low quality data generated by artificial intelligence (AI) models – often known as AI slop – is forcing more security leaders to look...