Tech
My Favorite Affordable 360 Rotating Pet Camera Is on Sale Right Now
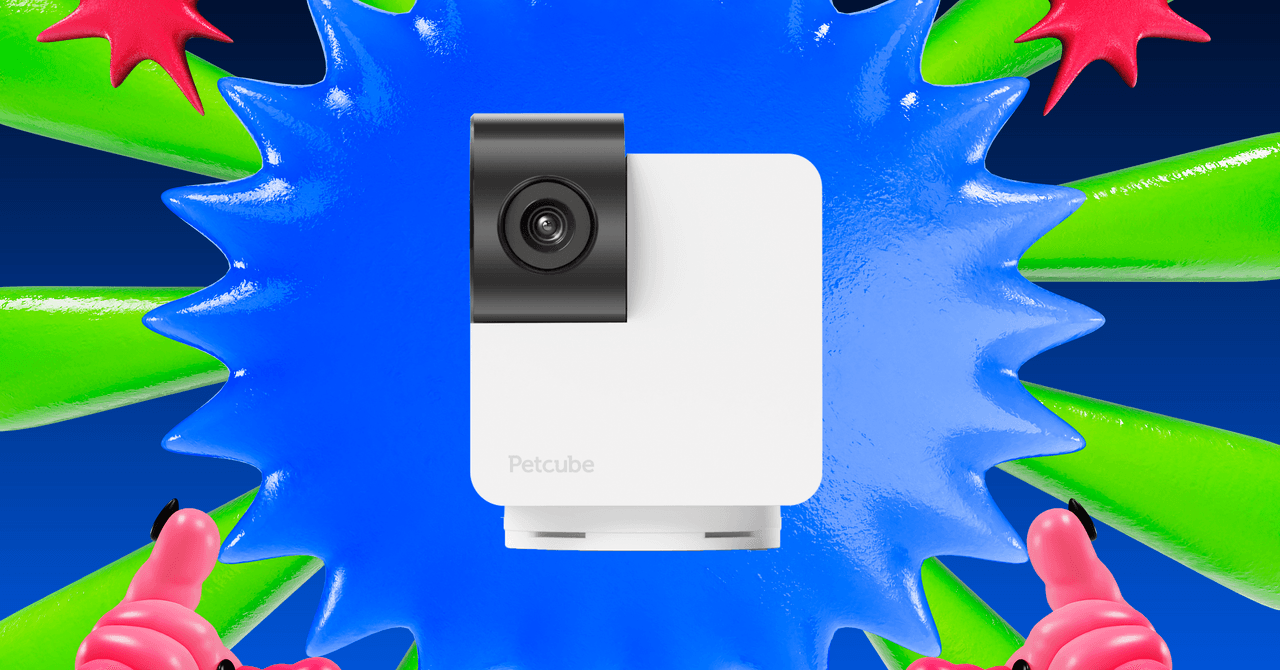
I’ve tested over a dozen pet cameras, and they are not all created equal. A pet camera sets itself apart from a regular indoor security camera with special, pet-related features like treat tossing or interactive two-way audio. Each usually has a subscription service, where you can review pet footage historically and get alerts when things seem amiss, like odd behavior or continuous barking or meowing.
At an already super-affordable price, this Petcube camera has 360 PTZ rotation capabilities (it can not only rotate horizontally, but vertically as well for full coverage), super clear 1080p HD resolution, the ability to digitally zoom eight times, two-way audio to speak and hear your pet, and night vision. It’s already super affordable at its usual $53, but for Amazon Prime Big Deal Days, it’s only $38, a crazy-good price for a pet camera of this caliber.
Although I love (and highly recommend) this camera, the Petcube Cam 360 suffers from one of the pitfalls I have with the rest of the brand’s lineup—the features are seriously limited if you don’t want to pay for Petcube’s upgraded Care plan (which starts at $4 a month). You need to subscribe to get the full benefit of the luxury pet camera; with the plan, you’ll get video storage capabilities, automatic pet detection, and automatic video recording capabilities. The price point for the subscription plan is one of the lowest I’ve seen while testing similar models, and I don’t think I’d be able to go on vacation with peace of mind again without the extra plan. (At less than I spend on a cup of coffee, I find the subscription plan to be really worth it.)
There’s an optional mounting that requires some tools, so setup is a bit tricky. (You’ll want to make sure it’s anchored since it needs to be stable while rotating.) The camera feed rotates smoothly without much lag, and because of the wide fish-eye lens and complete panning abilities, I was able to clearly see more of the room I was monitoring than the majority of other cameras I’ve tested.
There’s a bit of inherent risk when having indoor security cameras in your home, and with the camera’s new privacy mode, you can easily turn off the camera lens for even more security while you’re at home so that it’s not catching anything that you don’t want it to.
Petcube is running deals on most of the cameras from its pet camera line for Amazon’s Prime Big Deal Days, so I’d check its brand page for even more sales.
If you want to save even more on security for your whole house, check out the camera bundles below that are also on a steep discount.
Power up with unlimited access to WIRED. Get best-in-class reporting and exclusive subscriber content that’s too important to ignore. Subscribe Today.
Tech
This Backyard Smoker Delivers Results Even a Pitmaster Would Approve Of

While my love of smoked meats is well-documented, my own journey into actually tending the fire started just last spring when I jumped at the opportunity to review the Traeger Woodridge Pro. When Recteq came calling with a similar offer to check out the Flagship 1600, I figured it would be a good way to stay warm all winter.
While the two smokers have a lot in common, the Recteq definitely feels like an upgrade from the Traeger I’ve been using. Not only does it have nearly twice the cooking space, but the huge pellet hopper, rounded barrel, and proper smokestack help me feel like a real pitmaster.
The trade-off is losing some of the usability features that make the Woodridge Pro a great first smoker. The setup isn’t as quite as simple, and the larger footprint and less ergonomic conditions require a little more experience or patience. With both options, excellent smoked meat is just a few button presses away, but speaking as someone with both in their backyard, I’ve been firing up the Recteq more often.
Getting Settled
Photograph: Brad Bourque
Setting up the Recteq wasn’t as time-consuming as the Woodridge, but it was more difficult to manage on my own. Some of the steps, like attaching the bull horns to the lid, or flipping the barrel onto its stand, would really benefit from a patient friend or loved one. Like most smokers, you’ll need to run a burn-in cycle at 400 degrees Fahrenheit to make sure there’s nothing left over from manufacturing or shipping. Given the amount of setup time and need to cool down the smoker after, I would recommend setting this up Friday afternoon if you want to smoke on a Saturday.
Tech
Make the Most of Chrome’s Toolbar by Customizing It to Your Liking

The main job of Google Chrome is to give you a window to the web. With so much engaging content out there on the internet, you may not have given much thought to the browser framework that serves as the container for the sites you visit.
You’d be forgiven for still using the default toolbar configuration that was in place when you first installed Chrome. But if you take a few minutes to customize it, it can make a significant difference to your browsing. You can get quicker access to the key features you need, and you may even discover features you didn’t know about.
If you’re reading this in Chrome on the desktop, you can experiment with a few customizations right now—all it takes is a few clicks. Here’s how the toolbar in Chrome is put together, and all the different changes you can make.
The Default Layout
Take a look up at the top right corner of your Chrome browser tab and you’ll see two key buttons: One reveals your browser extensions (the jigsaw piece), and the other opens up your bookmarks (the double-star icon). There should also be a button showing a downward arrow, which gives you access to recently downloaded files.
Right away, you can start customizing. If you click the jigsaw piece icon to show your browser extensions, you can also click the pin button next to any one of these extensions to make it permanently visible on the toolbar. While you don’t want your toolbar to become too cluttered, it means you can put your most-used add-ons within easy reach.
For the extension icons you choose to have on the toolbar, you can choose the way they’re arranged, too: Click and drag on any of the icons to change its position (though the extensions panel itself has to stay in the same place). To remove an extension icon (without uninstalling the extension), right-click on it and choose Unpin.
Making Changes
Click the three dots up in the top right corner of any browser window and then Settings > Appearance > Customize your toolbar to get to the main toolbar customization panel, which has recently been revamped. Straight away you’ll see toggle switches that let you show or hide certain buttons on the toolbar.
Tech
The Piracy Problem Streaming Platforms Can’t Solve
“The trade-off isn’t only ethical or economic,” Andreaux adds. “It’s also about reliability, privacy and personal security.”
Abed Kataya, digital content manager at SMEX, a Beirut-based digital rights organization focused on internet policy in the Middle East and North Africa, says piracy in the region is shaped less by culture than by structural barriers.
“I see that piracy in MENA is not a cultural choice; rather, it has multiple layers,” Kataya tells WIRED Middle East.
“First, when the internet spread across the region, as in many other regions, people thought everything on it was free,” Kataya says. “This perception was based on the nature of Web 1.0 and 2.0, and how the internet was presented to people.”
Today, he says, structural barriers still lead many users towards illegal platforms. “Users began to watch online on unofficial streaming platforms for many reasons: lack of local platforms, inability to pay, bypassing censorship and, of course, to watch for free or at lower prices.”
Payment access also remains a major factor. “Not to mention that many are unbanked, do not have bank accounts, lack access to online payments, or do not trust paying with their cards and have a general distrust of online payments,” Kataya adds.
Algerian students also share external hard drives loaded with television series, while in Lebanon streaming passwords are frequently shared across households. In Egypt, large Telegram channels distribute content across different genres, including Korean dramas, classic Arab films and underground music.
“We grew up solving problems online,” says Mira. “When something is blocked, you find a way around it. It’s … a fundamental human instinct.”
Streaming Platforms Adapting
Andreaux says StarzPlay has tried to address some of the payment barriers that limit streaming adoption in the region. “StarzPlay recognized early that payment friction was a regional barrier to adoption,” he says. “That’s why we invested in flexible subscription models and alternative payment methods, including telecom-led billing options that make access easier across different markets.”
At the same time, international media companies are working together to combat piracy through the Alliance for Creativity and Entertainment (ACE), a coalition of film studios, television networks and streaming platforms that targets illegal distribution of films, television and sports content. Its members include global companies such as Netflix as well as regional players like OSN Group, which operates the streaming service OSN+ across the Middle East and North Africa.
Kataya notes that legitimate streaming platforms are still expanding across the region. “The user base of official streaming platforms has been growing in the region,” he says. “For example, Shahid, the Saudi platform, is expanding and Netflix has dedicated packages for the region.”
“Other players, like StarzPlay and local platforms in Egypt, are also finding their place,” Kataya adds. “Social media also plays a huge role, especially when a film is widely discussed or controversial.”
Piracy carries legal and security risks, Andreaux says. “Rather than just ‘free streaming’, piracy exposes consumers to malware and insecure payment channels,” he says. “It also weakens investment in local content by depriving creators of revenue and reducing jobs.”
But the structural barriers described by users across the region remain. For many viewers in North Africa and the Levant, the challenge is not choosing between piracy and legality—it is whether legitimate access exists at all.
-

 Business1 week ago
Business1 week agoUS Top Court Blocks Trump’s Tariff Orders: Does It Mean Zero Duties For Indian Goods?
-

 Fashion1 week ago
Fashion1 week agoICE cotton ticks higher on crude oil rally
-

 Entertainment1 week ago
Entertainment1 week agoThe White Lotus” creator Mike White reflects on his time on “Survivor
-

 Politics1 week ago
Politics1 week agoPakistan carries out precision strikes on seven militant hideouts in Afghanistan
-

 Business1 week ago
Business1 week agoEye-popping rise in one year: Betting on just gold and silver for long-term wealth creation? Think again! – The Times of India
-

 Sports1 week ago
Sports1 week agoBrett Favre blasts NFL for no longer appealing to ‘true’ fans: ‘There’s been a slight shift’
-

 Sports1 week ago
Sports1 week agoKansas’ Darryn Peterson misses most of 2nd half with cramping
-
 Politics1 week ago
Politics1 week agoUS Supreme Court strikes down Trump’s trade tariff measures


















