

AI agents like OpenClaw have recently exploded in popularity precisely because they can take the reins of your digital life. Whether you want a personalized morning...



An FBI informant helped run the Incognito dark web market and allegedly approved the sale of fentanyl-laced pills, including those from a dealer linked to a...



An analysis by WIRED this week found that ICE and CBP’s face recognition app Mobile Fortify, which is being used to identify people across the United...



An AI image creator startup left its database unsecured, exposing more than a million images and videos its users had created—the “overwhelming majority” of which depicted...



Amid a government shutdown that has dragged on for more than five weeks, the United States Congressional Budget Office said on Thursday that it recently suffered...



The Unique Identification Authority of India (UIDAI) has set up a high-level expert committee to make Aadhaar technology future-ready, with focus on scalability, data security, and...



“If there’s a camera that knows the cards, there is always some kind of underlying threat. Customers are gonna be essentially at the mercy of the...
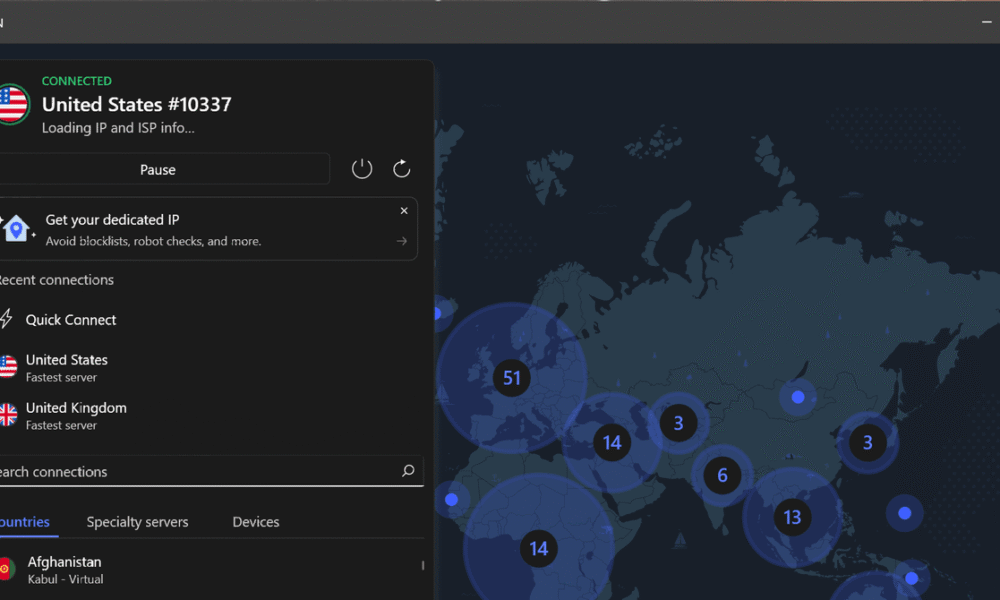
VPNs, Compared Other VPNs We’ve Tested EventVPN is the new hotness in the VPN world. It’s a free, ad-supported VPN that comes from ExpressVPN. Ads and...



Thousands of networks—many of them operated by the US government and Fortune 500 companies—face an “imminent threat” of being breached by a nation-state hacking group following...



Android devices are vulnerable to a new attack that can covertly steal two-factor authentication codes, location timelines, and other private data in less than 30 seconds. The...