Tech
Reinventing industry: Carbon capture technologies lead the charge against climate change

Researchers are testing a new method of capturing CO2 from energy-intensive industries and converting it into valuable chemicals and fuels.
In a potential game-changer for heavy industry, a magnesium-oxide mine in Greece received seven special containers in November 2024 with equipment designed to capture CO₂ and transform it into a valuable chemical, right there on site.
Long blamed for driving up the planet’s temperature, CO2 could now be converted into jet fuel for passenger aircraft—cutting emissions from both mining and transport.
“We just started capturing CO2, which is an amazing milestone,” said Dr. Haris Yiannoulakis, research and development manager at Grecian Magnesite, the producer of magnesium oxide.
The containers came from the Petrobrazi oil refinery in Romania. There, the carbon capture technology had been tried out as part of a project called ConsenCUS, involving seven countries and three test sites.
Getting down
The EU has set its sights on slashing greenhouse gas emissions by 55% by 2030, compared to 1990 levels. The ultimate goal: climate neutrality for industry by 2050.
ConsenCUS brings together new technologies to trap CO₂ from three notoriously hard-to-abate industries: oil refining, mining and cement production. These sectors face a double challenge, as CO₂ is generated both from burning fossil fuels and from the raw materials themselves.
For example, at the Grecian Magnesite mine site, raw material magnesite—a natural mineral found in rocks—is mined and heated up to 2,000°C to yield magnesium oxide. This material is crucial to a wide range of European industries, from steel and glass to fertilizers, animal feed and pharmaceuticals.
The downside, however, is that the thermal treatment releases CO2 both from the decomposition of magnesite and the fuel required for the process.
Three steps
The pilot plant in Greece is now tackling CO₂ conversion in three steps, explains Sara Vallejo Castaño, a chemical engineer at Wetsus research institute in the Netherlands.
First, a capture column separates CO₂ from factory gases, mixing it with water and potassium hydroxide. The CO₂ dissolves and reacts, forming potassium carbonate, which locks the gas in liquid form.
The second step uses electricity to raise the acidity of the solution, which releases CO2.
This method is simpler and greener than traditional heating or hazardous chemicals because it uses only electricity and water as resources.
A third step turns the CO2 into formic acid (or formate), a simple, naturally occurring chemical that can be found in nettles and ant bites.
“Formic acid is a well-known molecule used in the chemical sector,” said Dirk Koppert, the coordinator of ConsenCUS at New Energy Coalition, a nonprofit organization in the Netherlands.
One Dutch company, Coval Energy, already produces formic acid in this way from CO2. The acid is then fed to microbes to make fats and proteins. The proteins could be ingredients in cattle and fish feed, while the fatty acids could one day be used as a replacement for jet fuel.
Tough cement
The first testing site for the new technology was at Aalborg Portland in northern Denmark. This is one of the largest cement manufacturers in Europe, producing up to 1.8 million tons of gray cement and 0.8 million tons of white cement annually and operating since 1889.
Sustainability is a major selling point for its cement. The factory now uses non-fossil fuels for more than 30% of its heating needs for gray cement production, for example.
“We are reducing our dependence on fossil fuels and reducing CO2 emissions,” said Jesper Damfoft, sustainability director at the company.
But the manufacturing of cement still releases CO2 in the process.
The main cement ingredients in Aalborg are sand, dredged from the Limfjord waterway, and chalk from a local quarry. This calcium-rich chalk is heated to temperatures of about 1,500°C to produce lime (calcium oxide), which is essential for manufacturing cement.
When heated, the chalk’s carbon and oxygen atoms combine to form CO₂ gas, making cement production a major source of global emissions—by some estimates, accounting for 7%–8% of the world’s total.
A way forward is to capture and store CO2 underground, or put it to other uses, such as by making formic acid.
Under the EU’s emissions trading scheme, the price per excess ton of CO2 that companies have to pay stood at around €73 in June 2025, but it is expected to rise.
“Carbon prices are relatively low, but are predicted to be €150 per ton in 2030, and who knows what they will be beyond that,” said Yiannoulakis. Clearly, European industries must prepare.
The new capture technology remained in Greece until June for testing. The hope is to move the technology closer to a commercial plant and put it to work to capture CO2.
Working out the technicalities of how to capture CO2 gas and produce a desirable chemical required a dozen industry and research partners to come together, including those from universities in Canada and China.
“Without EU funds, we would not be able to build this project and test these technologies,” said Koppert.
Bringing communities on board
However, technical expertise is only part of the story.
Jacob Nielsenat from Robert Gordon University in Scotland has been investigating how to give citizens a voice in these new technologies.
He quickly realized that “lots of people didn’t know what carbon capture is, so we were asking people to give us their opinion on something they didn’t know anything about.”
Along with his colleague Kostas Stavrianakis, he invented a card game to prompt discussions on carbon capture. Both believe that results will come. “Most citizens are perfectly able to understand the complexities around these technologies,” said Stavrianakis.
He emphasized that the industry needs to talk to local people. “If you want a project to go ahead, it is always better to involve communities so they can feel part of it.”
This article was originally published in Horizon the EU Research and Innovation Magazine.
Citation:
Reinventing industry: Carbon capture technologies lead the charge against climate change (2025, August 22)
retrieved 22 August 2025
from https://techxplore.com/news/2025-08-reinventing-industry-carbon-capture-technologies.html
This document is subject to copyright. Apart from any fair dealing for the purpose of private study or research, no
part may be reproduced without the written permission. The content is provided for information purposes only.
Tech
If a Garmin Is Too Expensive, Consider Suunto’s Latest Adventure Watch

It’s always pleasing to see an array of physical buttons, and you get sizable ones too. You’re not going to miss these wide flat ones even when picking the pace up. The silicone strap has a nice stretch to it and while the button clasp is a bit awkward to get into place, this watch does not budge.
Suunto has jumped on the flashlight trend, with an LED light strip sat on the front of the case. You can adjust brightness levels and there’s SOS and alert modes to emit a very noticeable pulsating light pattern. This is a light I found useful rooting around indoors as well as on nighttime outings.
The biggest change is the introduction of a 1.5-inch, 466 x 466 AMOLED display. This replaces the dull, albeit very visible, memory-in-pixel (MIP) display. Suunto also ditched the solar charging that did require spending a significant amount of time outside to reap its battery benefits.
Adding AMOLED screens to outdoor watches has been contentious. The older MIP displays are just more power-efficient. The Vertical 2 is down by about 10 days from the older Vertical for what Suunto calls daily use.
Still, even if you’re putting its tracking and mapping features to use, you’re not going to be reaching for the charger every few days. After two hours of tracking in optimal GPS mode, the battery only dropped by 2 to 3 percent. The battery drop outside of tracking is also small and the standby performance is excellent as well.
Software Updates
Photograph: Michael Sawh
A more streamlined set of smartwatch features helps reserve battery for when it really matters. Unfortunately, I probably got better battery life because you don’t get phone notifications or responses if it’s paired to an iPhone instead of an Android. There’s also no onboard music player, but you do get a pretty slick set of music playback controls that are accessible during tracking.
Tech
Police do not have to explain to lawyer Fahad Ansari why they seized his phone data, says court | Computer Weekly

Police do not have to give a lawyer who was stopped, questioned and had his work mobile phone seized for forensic examination reasons for their actions, the UK’s high court has ruled.
The decision means that lawyers can be subject to counter-terrorism powers and have their privileged communications extracted and examined by the state, without having the right to know the case against them, said advocacy group Cage.
Fahad Ansari, who acts for Hamas in a legal appeal to have its proscribed status in the UK overturned, was stopped by police under Schedule 7 of the terrorist act while returning from holiday with his family last year.
The case is believed to be the first targeted use of Schedule 7 powers, which allow police to stop and question people and seize their electronic devices without the need for suspicion, against a practising solicitor.
The high court ruled on 4 March that police may present evidence about the reasons stopping Ansari in a closed court in front of a special advocate without Ansari or his lawyers being present – preventing Ansari or his legal team from learning the reasons why he was stopped.
Lawyers for Ansari argued the lawyer was entitled to be given a sufficient “gist” of the police’s case against him to enable him to disprove the police’s case, even if doing so would be damaging to national security.
Privileged material
Hugh Southey KC told the court in October 2025 that Ansari’s work phone contained data going back 15 years, including privileged material relating to his clients, and that any data extracted by the police should be deleted.
Ansari, an Irish citizen, argues that he was unlawfully stopped, detained and questioned under Schedule 7 of the Terrorism Act when he disembarked from a ferry with his family at Holyhead after visiting relatives in Ireland in August 2025.
The court was told last year that the phone contains details of at least 3,000 contacts, voice notes, memos, case papers, search terms and metadata, the overwhelming proportion of which is likely to be legally protected.
Justice Chamberlian found in a judgment published today the question was not whether any allegations made against Ansari by police in closed hearings were true, but whether police had a lawful basis for stopping and searching the lawyer at the time the search was carried out.
He found in a 15-page ruling that the use of Schedule 7 powers against Ansari to question him and seize his phone does not require any allegation to have been made against him, and that the seizure and retention of his personal information does not affect Ansari’s legal position.
The judge found that there were “substantial protections” in place to protect the integrity of legally privileged information, and that even if legally privileged material could be used against third parties, which it could not, they would enjoy the “full panoply of procedural rights”.
Ansari said he handed over the password to his phone after police warned him that to fail to do so would be an arrestable offence. He said that police also questioned him about Palestine Action, a direct action protest group that was proscribed under the Terrorism Act 2000, though Ansari has no connection with the group.
South Wales Police, which is responsible for counter-terrorism in Wales, has denied that Ansari was stopped because of his political views, and maintains that asking him questions about proscribed organisations is not unlawful.
Ansari, a registered freelance solicitor, became consultant at Duncan Lewis Solicitors, where he specialises in national security and complex human rights cases, after training at Fisher Meredith LLP and Birnberg Peirce.
Speaking after the judgement, Ansari said he would challenge the judge’s order that the police should not disclose their reasons for stopping him in open court.
“Seven months on, I remain in the dark about why counter-terrorism police detained and interrogated me and continue to examine the contents of my work phone,” he added. “I am exploring all options to challenge this dangerous precedent.”
Commenting on the case, Anas Mustapha, head of public advocacy at Cage, said that allowing secret evidence was a “thin end of the wedge” that could undermine justice. “Once courts accept that the state can accuse someone without revealing the accusation, the foundations of justice begin to collapse,” he added.
“The legal profession now faces a serious question: whether it will continue to accommodate secret courts through mechanisms like the special advocate system, or whether it will begin the difficult work of rolling back a process that has steadily eroded open justice for more than two decades,” said Mustapha.
Tech
These $500 Windows Laptops Show That the MacBook Neo Has Serious Competition
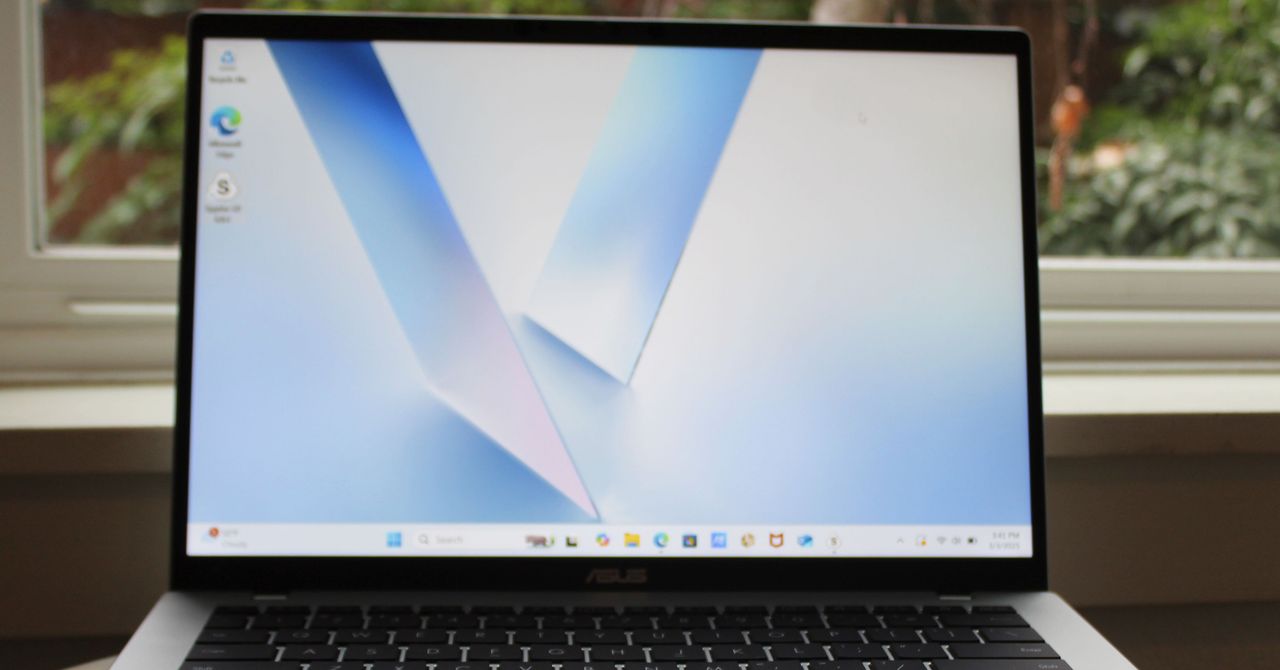
Today, Apple announced its new budget MacBook. At $599, it looks seriously impressive. While I haven’t tested its performance, battery life, or display just yet, it may end up being hard to beat at that price based on some of the specs alone.
But that doesn’t mean the competition isn’t there. I want to recommend a couple of Windows laptops deals that offer various advantages over the MacBook Neo, showing where the Neo has both strengths and weaknesses.
First, check out this Asus Vivobook 14, a laptop I’ve been happy to recommend as a budget computer for the past year. In many ways, this is the Windows version of a laptop like the MacBook Neo. It uses a highly-efficient ARM chip, the Qualcomm Snapdragon X, meaning it gets great battery life and performs admirably in daily tasks. It’s not quite as thin or light as the MacBook Neo, but it’s fairly portable for a laptop at this price.
Unlike the MacBook Neo, the Vivobook 14 comes with 16 GB of RAM and 512 GB of storage. That’s twice what you get in the MacBook Neo’s starting configuration. Right now, this configuration of the Vivobook 14 is on sale for $539. That’s a killer deal for those specs. It even comes with a healthier mix of ports, including HDMI, two USB-A, one USB-C, and a headphone jack. That also means it can support two external displays unlike the MacBook Neo, which can only handle just one.
Don’t get me wrong—I’m not at all saying the Vivobook 14 is a slam dunk over the MacBook Neo. Based on specs alone, I know the Vivobook 14 is a serious step down when it comes to the display. It’s less sharp, stretched across a larger screen, and the color performance isn’t so good. The Vivobook 14 maxes out at 280 nits, whereas Apple says the MacBook Neo can go all the way up to 500 nits. I have a hunch that the MacBook Neo will deliver a much better display in just about every regard.
There’s also the touchpad. It’s a little clunky to use, which is typical of budget Windows laptops. This is just a guess—but the touchpad on the MacBook Neo will likely feel smoother. It’s a mechanical trackpad (unlike the MacBook Air’s haptic feedback trackpad), but Apple has almost never made a bad trackpad.
If you’re not convinced by the Asus Vivobook 14, I’d also recommend the HP OmniBook 5, which is currently on sale for $500 and uses the same Snapdragon X chip. While it only has 256 GB of storage, it has a much better screen than the Vivobook 14, using an OLED display. It’s not any brighter than the Vivobook 14, but it gives you far better color performance and contrast. It’s also just 0.50 inches thick, matching the MacBook Neo exactly in portability.
-

 Business6 days ago
Business6 days agoIndia Us Trade Deal: Fresh look at India-US trade deal? May be ‘rebalanced’ if circumstances change, says Piyush Goyal – The Times of India
-

 Business7 days ago
Business7 days agoAttock Cement’s acquisition approved | The Express Tribune
-

 Politics1 week ago
Politics1 week agoWhat are Iran’s ballistic missile capabilities?
-

 Politics1 week ago
Politics1 week agoUS arrests ex-Air Force pilot for ‘training’ Chinese military
-

 Business1 week ago
Business1 week agoHouseholds set for lower energy bills amid price cap shake-up
-

 Fashion7 days ago
Fashion7 days agoPolicy easing drives Argentina’s garment import surge in 2025
-

 Sports6 days ago
Sports6 days agoLPGA legend shares her feelings about US women’s Olympic wins: ‘Gets me really emotional’
-

 Fashion6 days ago
Fashion6 days agoTexwin Spinning showcasing premium cotton yarn range at VIATT 2026